Cybersecurity failures should be considered global risks—and they are among the most likely global risks to occur over the next five to 10 years. We have already seen a significant increase in the number of cyberattacks since 2006, and they have only accelerated during the pandemic. The attack surface for cyber threats has increased drastically owing to remote connectivity, integration with enterprise networks, and the advent of the Internet of Things (IoT). Companies have been forced to think about cybersecurity in their strategic decision-making processes and risk management.
According to a recent analysis of ICS incidents, 80% of all incidents are unintentional, attributed mainly to routine jobs executed by the organization's IT/OT personnel, malware, and network devices misconfigurations. By addressing these problems, organizations can significantly reduce the likelihood of a cybersecurity incident and overall risk.
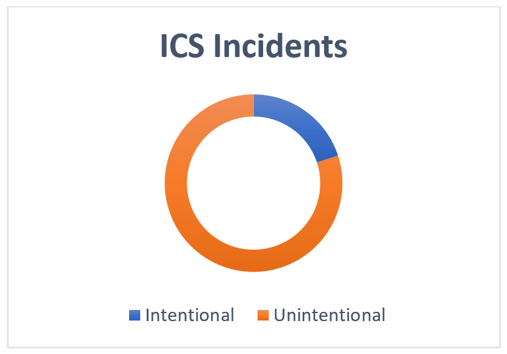 Diagram courtesy of the author.
Diagram courtesy of the author.
The ISA/IEC 62443 series of standards suggests that end users take a lifecycle approach to implementing cybersecurity for their assets from the conceptual design stage to installation and commissioning, O&M, and decommissioning. This ensures complete protection throughout the lifecycle of an asset. While there is no single recipe to implement cybersecurity, below are some of the guidelines that asset owners can follow to remediate some their problems immediately.
Access and Use Control
Physical Access
All facilities should have physical access control measures in place to avoid unauthorized personnel entrance to control rooms, engineering rooms, and control cabinets rooms. The areas should be labelled as restricted, and all entrances should be logged with personal identity and purpose. Further enhancements commonly employed include installation of CCTV in these rooms and automatic RFI/ fingerprint entrance.
Logical Access and Use Control
All users with access to the control systems/PLCs and network devices should be uniquely identifiable and authenticated. User profiles with their rights against each role must be clearly defined, and a role-based access control list must be maintained for all users. This includes continuously reviewing and updating the list—personnel who are transferred within the company and those who leave should be removed from system access. It must be noted that users should only have access to the actions they need to execute.
Another problem frequently observed is that network devices/PLCs and control systems continue to keep their default accounts intact with all the administrator privileges as a convenient way to remember different passwords. This often provides unauthorized access to users, which allows a user with a low skill level to make changes that could potentially take down your whole network with serious consequences. It is important that all default accounts/passwords are changed. Additionally, any unused accounts must be removed. (Bonus: another best practice involves blocking all unused ports in the system.)
Control system administrators need to ensure that they adopt a strong policy on passwords. Minimum length and complexity should be defined, and passwords should be frequently changed.
To prevent unauthorized access, all users must also be advised to ensure that the system is locked out when not in use, or while they are away.
Remote Access
Asset owners are often required to provide vendors with remote access. Remote access should be limited to only essential business requirements, and only enabled when necessary. Controls can include—but are not limited to—multi-factor authentication, one-time logins/passwords for a limited time period, and communication channel encryption. Remote access software can be installed after making sure that any existing vulnerabilities are patched, as well as changing default ports and enforcing strong usernames and passwords.
Training and Awareness
With the increasing trend in cybersecurity incidents, people must be the focus of any cybersecurity program’s strategy. Many incidents have been attributed to social engineering, whereby field technicians and control room operators became victims while plugging in an affected USB, providing access to restricted areas, and so on. To create better awareness, employees need to understand what can go wrong and what they can do to prevent such incidents. ISA/IEC 62443-2-1 specifies that qualified personnel are assigned with roles and responsibilities specific to cybersecurity.
The following list includes some practical ways to increase cyber risk awareness:
- Develop employees’ understanding of the ways that cybersecurity gaps can lead to safety incidents, equipment damages, and production loss
- Train engineers and operators to recognize events or activities which can lead to an ICS incident (in the recent Florida water hack, the plant operator played a critical role, preventing a potentially deadly increase in the concentration of chemicals)
- Develop actionable do’s and don’ts
- Arrange integrated sessions between IT and OT personnel to understand differences and how each can benefit from one another
- Conduct internal/external trainings
- Start an email awareness campaign on specific themes like password protection, portable media use, and so on
Cyber Risk Assessment
The basic principle for control applications is “you cannot control what you cannot measure.” While the steps mentioned above do help in improving the cybersecurity, they cannot be considered as a complete solution.
Each facility has different risks, conditions, and challenges. This requires asset owners to conduct a Cyber PHA (process hazard analysis) and a risk assessment to identify high-risk areas and develop strategies (countermeasures) to address those risks. All asset owners should plan to conduct these risk assessments as per ISA/IEC 62443, so that only the required safeguards covering all three aspects—people, processes, and technology—are implemented. This will ensure that users do not invest on any unassessed technological solutions that do not provide gains and necessary protection required against all cyber threats.
Conclusion
In summary, asset owners should focus on their existing processes and personnel to improve their overall cybersecurity hygiene. Strengthening access and use controls, as well as training and awareness, are key steps toward a successful cybersecurity program. Additionally, these steps prepare their teams to take the next steps toward a holistic approach by doing a cybersecurity assessment and making improvements in their existing technology.
Interested in reading more articles like this? Subscribe to ISA Interchange and receive weekly emails with links to our latest interviews, news, thought leadership, tips, and more from the automation industry.
See also: Here’s a comprehensive guide from Technology Advice in choosing the right enterprise risk management software for your business organization.




