This post was authored by Steve Mustard, an industrial control system and cybersecurity consultant, and author of the ISA book Mission Critical Operations Primer.
In 2013 President Obama issued Executive Order 13636, titled "Improving Critical Infrastructure Cybersecurity." The executive order instructed the National Institute of Standards and Technology (NIST) to develop a voluntary cybersecurity framework that would provide a "prioritized, flexible, repeatable, performance-based, and cost-effective approach for assisting organizations responsible for critical infrastructure services to manage cybersecurity risk.
The definition of "critical infrastructure" in the executive order is:
"Systems and assets, whether physical or virtual, so vital to the United States that the incapacity or destruction of such systems and assets would have a debilitating impact on security, national economic security, national public health or safety, or any combination of those matters"
The state of cybersecurity
Given the availability of a variety of standards for cybersecurity management, people have asked why a cybersecurity framework is required. Furthermore, many of these standards have been in existence for many years. Many people believe that the requirements of these standards are being followed, so further similar standards will not help.
There are many publicly available reports on cybersecurity attacks, and there has been a common theme:
- Ninety seven percent were avoidable with basic or intermediate security controls.
- Ninety two percent were discovered by a third party.
- Twenty percent of network intrusions involved manufacturing, transportation, and utilities.
- Seventy six percent of network intrusions exploited weak or stolen credentials.
- So despite the availability of standards, it is clear that many organizations are not applying them to the degree required.
The Repository of Industrial Security Incidents produces an annual report that focuses specifically on industrial control systems (ICS). These reports have similar conclusions to those from Verizon. T
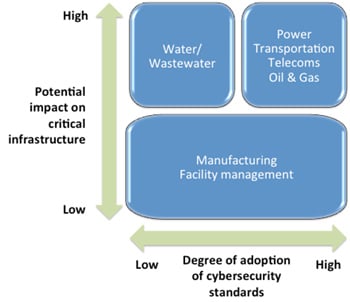
The statistics from Verizon cover all sectors and industry types. Within industrial automation-oriented sectors, the situation varies considerably. Many such organizations have mandatory cybersecurity standards (i.e., NERC CIP in the power industry), and their cybersecurity management programs are good. However many organizations that have a potentially high impact on critical infrastructure (e.g., water or wastewater organizations) have a much lower degree of cybersecurity management adoption.
There are many reasons for this situation, and they include:
- lack of awareness in organizations, in particular at the top of the organization
- misunderstanding the level of risk an organization has (e.g., "that only happens to other companies," "this has never happened before")
- inability to quantify the risk in likelihood or impact terms, resulting in inappropriate level of investment
- lack of adequate training in cybersecurity good practice, especially in regards to basic controls, such as good password management, backups, and malware protection
The purpose of the NIST Cybersecurity Framework is to help tackle some of these issues. The cybersecurity framework is not another standard. Instead it is a high-level concept that brings together relevant standards and sets them in an appropriate context.
ISA offers standards-based industrial cybersecurity training, certificate programs, conformity assessment programs, and technical resources. Please visit the following ISA links for more information:
- ISA Global Cybersecurity Alliance
- Cybersecurity Resources Portal
- Cybersecurity Training
- IEC 62443 Conformance Certification
- ISA Suite of Security Standards
- ISA Family of Standards
- ISA/IEC 62443 Cybersecurity Certificate Programs
About the Author
Steve Mustard, author of the ISA book, Mission Critical Operations Primer, is an independent automation consultant and subject-matter expert of ISA and its umbrella association, the Automation Federation. He also is an ISA Executive Board member. Backed by nearly 30 years of software development experience, Mustard specializes in the development and management of real-time embedded equipment and automation systems, and the integration of real-time processing, decision-support and other disparate systems to improve business processes. He serves as president of National Automation, Inc. Mustard is a recognized authority on industrial cybersecurity, having developed and delivered cybersecurity management systems, procedures, training and guidance to multiple critical infrastructure organizations. He serves as the chair of the Automation Federation’s Cybersecurity Committee. Mustard is a licensed Professional Engineer, UK registered Chartered Engineer, a European registered Eur Ing, an ISA Certified Automation Professional (CAP) and a certified Global Industrial Cybersecurity Professional (GICSP). He also is a Fellow in the Institution of Engineering and Technology (IET), and a senior member of ISA.
A version of this article also was published at InTech magazine.



