This article was written by Scott Hillman, an independent consultant formerly with Honeywell Process Solutions.
When it comes to the most important aspects of efficient and effective plant operations, having proper physical security measures in place is still just as critical as the flow of raw materials, efficient process control, a competent workforce, and yes, cybersecurity measures. Like cybersecurity, the core concept of physical security is to detect and prevent an intrusion. Even though it is a different kind of intrusion, consequences of failing to protect can be disastrous. For this reason, it is clear that physical security cannot be placed on the backburner.
What steps, therefore, should plants take and make sure they do not neglect when it comes to having an effective physical security system in place amid the cyber hoopla? The common approach remains "defense in depth." This is similar to the "layers-of-protection" philosophy used when designing integrated safety systems-i.e., ensuring multiple measures are deployed on top of each other so if one layer is penetrated, another one is there to further safeguard. With this system, no one layer or measure is responsible for being a catch all.
But recent trends in manufacturing (process safety incidents, increasingly tighter budgets, the aging workforce, regulations, and increased demand) are forcing plants to dig a little deeper with the defense-in-depth concept. Specifically, defense in depth means more today than just adding layers of protection-it means ensuring those layers are folded into the core plant controls along with other subsystems.
Why defense in depth?
At all times, plants are charged with protecting their people, assets, and the environment. At its core, physical security helps achieve this objective by keeping the wrong people on the right side of the fence to prevent incidents of vandalism, theft, and malicious acts.
Because protecting people, assets, and profitability demands a holistic point of view, visualizing what physical security at a plant looks like can be difficult, as the concept is fairly abstract. The most obvious ways to protect facilities are physical: fences, barricades, and guards. But these safeguards provide only one layer, and physical security is more than a barbed-wire fence around a facility. It involves tracking and managing people and assets, complying with federal and industry regulations, monitoring premises with video, implementing access control, and establishing perimeters. There is no one-size-fits-all approach when considering how to best implement or strengthen a physical security plan, but there are blueprints from successful implementations that can provide a guide in terms of steps to follow and considerations to take.
An integrated approach must provide protection from their process control room to the perimeter, protecting all assets of a plant. It should include components such as video surveillance, access control, perimeter intrusion detection, and command centers that work together to provide an extensive method of protection for plants.
Having such an integrated physical security solution in place allows plant managers and operators to ensure their top safety priorities-things like stable control of the plant-are secured while concentrating on other components that factor in to the safe, secure operation of a plant. For this reason, the design of an integrated system must be clearly aligned with existing safety and process control systems. This approach allows certain layers of protection to deter incidents in the first place, while others can provide detection and alerting and associated guidance.
Layers can either be automated or require human interaction. Some layers offer easily quantifiable risk-reduction benefits but require the risks all be identified before. Others are less tangible and offer softer benefits.
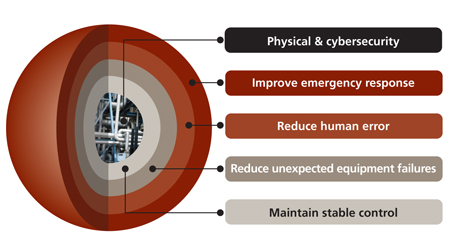
At the core of the layered architecture is a well-designed and implemented process design that is the embodiment of the business, safety, and production considerations necessary for effective operations. The process must be controlled by a secure process control network that extends across the entire plant and business networks. Managing the plant's assets ensures the process design continues to function as intended, all while protecting the plant from pending incidents with an early indication of failing assets.
With the correct work practices and technology in place, in the event an abnormal situation does occur disrupting safe operations, an emergency response plan can be executed, controlled, and monitored to minimize the impact of the incident.
Video: A key integration ingredient
When operating under a plant security concept like defense in depth, it is necessary to have technologies available that can integrate with each other to reinforce the layered protection necessary in securing a plant. One of the key ingredients here is video surveillance technology. Much of the ability to integrate video with the control room stems from the installation of a digital video system. Since the key to a successful video system is being able to manage and filter through the vast amounts of video information captured continuously, having a digital video system available offers much greater flexibility.
For instance, connecting the closed-circuit television system with a plant's control room, operators have widespread access and monitoring capabilities that touch all corners of the facility. Operators can perform all viewing, recording, and archiving and retrieval functions from a single interface.
With digital video able to be easily integrated into one platform, something like monitoring an entirely separate facility hundreds of miles away can now be done in a central control room-this is especially critical today, considering many new sites are smaller and more widely dispersed than the massive facilities that were commonly being built only a few decades ago. A distributed video architecture (DVA) allows security personnel to view video from multiple digital video systems on one virtual platform, whether across a single campus or across the country.
DVA is particularly beneficial for multi-site and critical infrastructure applications because it provides central monitoring and control of all cameras and equipment on the network. Digital video in a distributed architecture is completely scalable, making the extension of a video system much more cost-effective.
Integrating digital video systems with the control room also reduces the hit to the wallet that plants face when deploying traditional surveillance measures. With scanning and alerts available 24 hours a day, the speed and accuracy in which operators can respond to abnormal situations is increased. Vital plant events are responded to appropriately, and possibly, costly plant shutdowns are avoided. Video deployment costs are also reduced, with one system able to integrate disparate systems like security, fire and gas, and control. Streamlined video surveillance certainly reduces operating costs but also reinforces the oversight and response ability for plant operators.
Finding starting point
To effectively secure a facility, plant managers must take an inside-out approach-they must start with securing the heart of their plants (the process control network) and gradually build layers of protection that extend all the way to the property perimeter.
There are several thorough steps that must be taken to achieve these layers of protection and ensure effective integration, such as:
- A site vulnerability assessment
- Understanding available security systems
- Determining mitigation steps
- System implementation
- Reassessment
A site vulnerability assessment determines possible holes in a plant's overall security system and prioritizes improvement opportunities. When completed, the assessment will have examined the impact of a security breach and the effect it can have on security personnel and process operators and will have examined the gaps that exist in the plant's physical security application.
After the site vulnerability assessment, a thorough understanding of the latest security technology is necessary to determine threat mitigation steps and how to fill the observed security gaps. Physical security subsets like access control, visitor management, video surveillance, and perimeter and intrusion control all factor in to the effectiveness of plant security, and the understanding of the latest technologies and their advancements is essential to having an effective, holistic approach to security.
Once vulnerabilities are categorized and prioritized, mitigation steps must be identified. Mitigation steps are unique to each site, but practices like strengthening the situational awareness of process operators and security personnel can help integrate process control and security systems. Security personnel are made more aware of non-security incidents, and process personnel are made more aware of security incidents. This type of compromise and awareness creates a more effective, holistic approach to industrial security.
System implementation will create an integrated architecture that will allow plant operations staff to improve collaboration and responsiveness to reduce security risks. As mentioned, a DVA can help integrate security and process systems, and its ability to tie third-party systems together makes it important when making integration a reality. Without a standard such as DVA, it is difficult to achieve effective communication that allows a site to be more aware of a security issue, and awareness allows for increased responsiveness.
Integrated-the new norm
The processing industry is facing real challenges as technology is forever advancing, seasoned industry professionals are retiring, and the business environment of the new global economy pressures managers in different directions. At the same time, moral, regulatory, and insurance requirements must be met in terms of maintaining a safe and secure workplace.
Research has shown abnormal situations cost many millions of dollars. Manufacturers pay dearly for these catastrophes. There are numerous catastrophes that can be cited, but they all indicate the need for focusing on layers of protection to provide a safer work environment, while at the same time increasing process availability and reducing total cost.

When fully executed and online, an integrated approach to plant security helps customers improve their business performance and peace of mind. It includes independent, yet interrelated layers of protection to deter, prevent, detect, and mitigate potential threats, while increasing the flexibility, scalability, and cost effectiveness of the entire system.
Implementing technology-driven solutions may provide some relief to the pending safety pressures. However, not until a site considers independent yet interrelated layers of protection to deter, mitigate, and prevent potential threats will there be a satisfactory solution to the physical security problem.
About the Author
Scott Hillman is and independent consultant. He was formerly global solutions director for Honeywell Process Solutions. He has over 30 years of process automation experience and is based in Phoenix, Ariz.
A version of this article also was published at InTech magazine.




