There are moments when the occurrence of errors could not imply the observation of any kind of disturbance, which may be capable of disrupting the operation of a computer-based system. If we extrapolate such a concern to the communication network itself, we realize how important it is to deal with network errors, preventing the propagation of any type of issue to the applications and protocols executed on top of the established communication infrastructure [1-4]. From the wired realm [1-2] we have acquired fundamental lessons, emphasizing the importance of securing dependability and timeliness properties during the network operation. The requirement of holding such properties in the domain of wireless communications is not different [3]. It is, indeed, essential to offer resilient real-time wireless communications in the presence of different sources of disturbances, from communication medium impairments to node mobility [5].
We all could agree that dependability and timeliness are key factors for any kind of wireless real-time network, which can be established on top of any suitable standard such as the general-purpose IEEE 802.15.4 [6], or ISA100.11a [7] for industrial automation. However, the question is: How could we secure such fundamental factors? In this article, we visit the roots of the network operation for securing its provided communication service as a dependable, safe, and timely asset for industrial automation. Instead of focusing on the results we need to deliver, we address aspects related to dependability and timeliness properties of the network operation, establishing a solid foundation to build resilient real-time wireless communications, which imposes little or no modification to the current networking standards.
A Dependable and Timely Wireless Network Service
There is no single moment when safety-critical environments do not refer to the fundamental requirement of securing a safe operation of the entire ecosystem. The communication network is part of it, and its operation must be as safe as the other parts of the system.
The Medium Access Control (MAC) layer is the rightful candidate to assume the role of coordinator for any safety-critical communication. However, the unreliable nature observed in the design of the MAC layer does not allow it to get into such a position. Delegating such a task to higher layer protocols and applications does not seem to be a suitable strategy, as such higher entities cannot observe, and account the specific disturbances, and its associated drawbacks occurred at such a low-level [3].
For transforming the MAC layer into a dependable, timely, and resilient entity, with the ability of monitoring and controlling any temporal aspect of communications, ensuring the safety of the entire system in between, we need the establishment of a trustworthy network service on top of its exposed service interface [8]. The premise to rely on such a service is supported by the following statement:
If no real-time guarantees can be offered within communications at one hop of distance, no real-time guarantees can be offered within multiple-hop communications at all.
To be considered trustworthy, the network service must be dependable. It must be capable of dealing with any type of issue happening during the communication process of two or more entities (e.g., applications), from the loss of data to the temporary disruption of network communications, dubbed network inaccessibility [9]. The network service also must not offer any threat to the safety of the system, implying the requirement to deliver communications just on the right time, i.e., a dependable and timely operation. Such trustworthy network service results from the use of a resilient real-time wireless architecture, such as the one proposed in reference [8].
The Wi-STARK Architecture
Wi-STARK is a layered and component-based architecture that aims to establish the required foundation for supporting (hard) real-time communication services on the wireless realm [8]. Wi-STARK has been designed to fit in the lowest levels of the networking protocol stack, based on results obtained from a case study of the IEEE 802.15.4 standard.
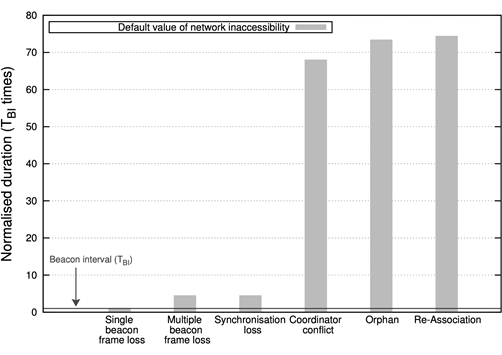
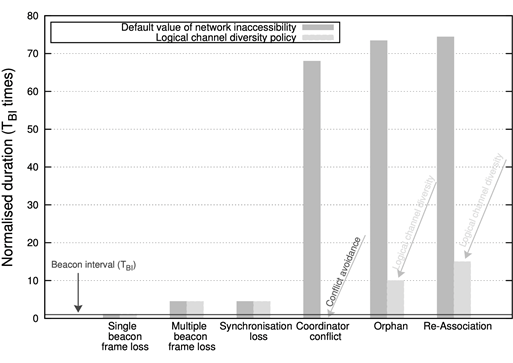
The requirement of addressing the issue of temporary network partitions has been highlighted by the characterization of network inaccessibility in IEEE 802.15.4, which has been presented in reference [9]. Due to the prohibitive durations obtained, which are illustrated in Figure 1, strategies to deal with the presence of network inaccessibility in the wireless realm have been designed and applied, reducing its negative charge significantly, as illustrated in Figure 2.
Figure 1: Characterization of Network Inaccessibility in IEEE 802.15.4 Wireless Networks [10]
Figure 2: Reducing Network Inaccessibility in IEEE 802.15.4 Wireless Networks [10]
The Wi-STARK architecture has an intrinsic design that can be incorporated in Commercially Off-The-Shelf (COTS) components. A visual representation of the Wi-STARK architecture is illustrated in Figure 3; it builds up on the RF transceiver exposed interface, which integrates basicMAC and the Physical Layer. In Figure 3, the two distinguished but interdependent internal layers are highlighted: The Mediator Layer and the Channel Layer.
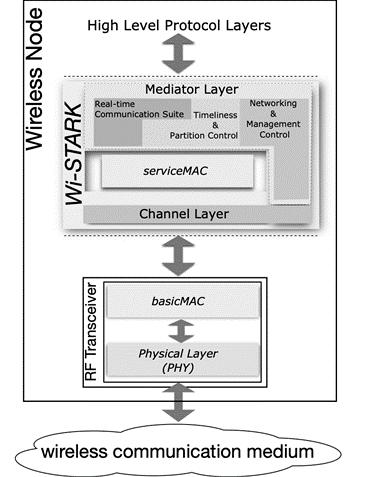 Figure 3: The Wi-STARK Architecture
Figure 3: The Wi-STARK Architecture
The Mediator Layer is a real-time communication service layer that enables high level entities to transmit time-sensitive data through the network. The Channel Layer is a control and monitoring layer, which controls and monitors the way communication channel(s) and RF transceiver(s) are utilized for real-time communication between wireless nodes. The Wi-STARK architecture design provides two fundamental guarantees to the high-level protocols and applications:
- Time-bounded communications
- Resilience against failures on the wireless communication medium
In terms of numbers and evaluation of worst-case scenarios, any guarantee offered depends directly on the technology in use. Because of such dependency, all guarantees offered by the Wi-STARK architecture are described in an abstract form, requiring a direct mapping with technology to obtain concrete numbers regarding dependability, timeliness, and safety properties of the network operation. In other words, Wi-STARK offers the capability to adapt, with little or no extension, to the characteristics of the wireless network standard in use (e.g., IEEE 802.15.4, ISA100.11a, or WirelessHART), where for each one of them we may have more strict or relaxed guarantees provided.
If you are interested in going into the technical details of our contributions, please see the following complementary white paper.
About the Authors
Jeferson L.R. Souza is the Founder, Writer, and all in between at NeartWord. He is also an Independent Software Engineer Consultant with expertise in the development of backend solutions, through the use of Java technologies. He received a M.Sc degree in Computer Science from Federal University of Santa Catarina (UFSC), in Brazil, where he is currently a Ph.D. candidate. As a complement, he has completed a postgraduate course in Crime Scene Investigation & Forensics Science from IPOG – Instituto de Pós-graduação e Graduação, also in Brazil, becoming an Expert in Crime Scene Investigation (CSI). His research interests are focused on Fault-Tolerant, Dependable, and Real-Time Networked Architectures, which can be applied to different domains: from WebServices to Medium Access Control (MAC) layers and protocols. Jeferson has worked in some national (European) and International projects related to his research interests. The Karyon Project is the most notable one.
Frank Siqueira is a Professor at the Department of Informatics and Statistics of the Federal University of Santa Catarina (UFSC), in Brazil. He received a Ph.D. degree in Computer Science from Trinity College Dublin (TCD) and was a research associate at the University of Sydney, Australia. He is a founding member of UFSC’s Distributed Systems Research Laboratory (LaPeSD), where he conducts research on the following subjects: Web Services; Semantic Web; Quality of Service; and Distributed Databases.
References
[1] Veríssimo, P., Rufino, J., and Rodrigues, L.. Enforcing Real-Time Behaviour on LAN-Based Protocols. In the 10th IFAC Workshop on Distributed Computer Control Systems, September 1991.
[2] Rufino, J., Almeida, C., Veríssimo, P., and Arroz, G. Enforcing Dependability and Timeliness in Controller Area Networks. In the 32nd Annual Conference of the IEEE Industrial Electronics Society (IECON), Paris, France, November 2006.
[3] Souza, J. L. R., Pinto, R., and Rufino, J. Mechanisms to Enforce Dependability and Timeliness in Wireless Communications. In the IEEE International Conference on Wireless Space and Extreme Environments (WiSEE), Noordwijk, Netherlands, October 2014.
[4] Souza, J. L. R. and Rufino, J. Low Level Error Detection for Real-Time Wireless Communications. In the 13th International Workshop on Real-Time Networks (RTN) - In conjunction with the 26th Euromicro International Conference on Real-Time Systems (ECRTS), Madrid, Spain, July 2014.
[5] Souza, J. L. R. and Rufino. J. An Approach to Enhance the Timeliness of Wireless Communications. In the 5th International Conference on Mobile Ubiquitous Computing, Systems, Services and Technologies (UBICOMM), Lisbon, Portugal, November 2011.
[6] IEEE 802.15.4. Part 15.4: Wireless Medium Access Control (MAC) and Physical Layer (PHY) Specifications for Low-Rate Wireless Personal Area Networks (WPANs) - IEEE standard 802.15.4. 2011.
[7] ISA100 Working group. ANSI/ISA-100.11a-2011 Wireless Systems for Industrial Automation: Process Control and Related Applications. 2011. Available at https://www.isa.org/products/ansi-isa-100-11a-2011-wireless-systems-for-industr.
[8] Souza, J. L. R. and Rufino, J. The Wi-STARK Architecture for Resilient Real-Time Wireless Communications. ACM SIGBED Review - Special Issue on the 4th Embedded Operating Systems Workshop (EWiLi 2014), 11(4), December 2014.
[9] Souza, J. L. R. and Rufino, J. Characterization of Inaccessibility in Wireless Networks - A Case Study on IEEE 802.15.4 Standard. In Achim Rettberg, Mauro C. Zanella, Michael Amann, Michael Keckeisen, and Franz J. Rammig, editors, Analysis, Architectures and Modelling of Embedded Systems: Third IFIP TC 10 International Embedded Systems Symposium IESS 2009, Langenargen, Germany, September 14-16, 2009, Proceedings, volume 310, pages 290–301. Springer, 2009.
[10] Souza, J. L. R. and Rufino, J. Analysing and Reducing Network Inaccessibility in IEEE 802.15.4 Wireless Communications. In the 38th IEEE Conference on Local Computer Networks (LCN), Sydney, Australia, October 2013.