The pandemic has changed our lives in many ways. Not only have we changed our work behavior and culture, but our consumption of technology has also changed. While the new technologies and especially platforms like the Internet of Things (IoT) have eased the way we work and perform our tasks, they have also given a bigger opportunity to cybercriminals.
Due to the pervasiveness and magnitude of the coronavirus pandemic, there has been a huge increase in the number, speed, and scale of cyberattacks. IoT devices specifically saw an increase in cyberattacks, which led to the unavailability of IoT networks due to leaked access credentials. In fact, even new home appliances are infiltrating corporate networks.
Statistics from various sources show that cyberattacks have been on the rise during COVID-19. According to research performed by Checkpoint, “71% of security professionals have noticed an increase in security threats or attacks since the beginning of the Coronavirus outbreak.”
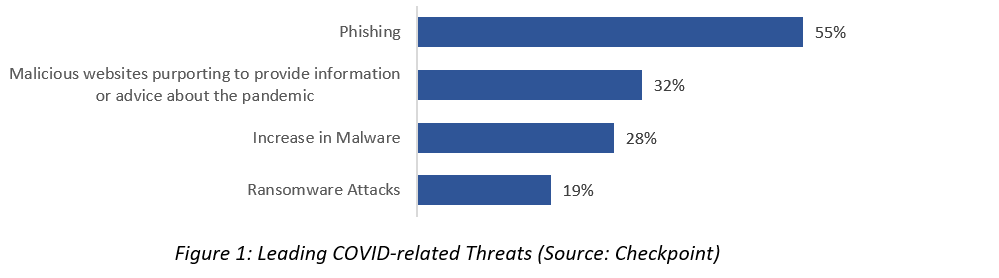
The most notable types are:
- Email phishing campaigns
- Fraudulent web pages or sites claiming to collect donations or advice
- Malware
- Ransomware
 The pandemic immediately forced most companies to figure out how to build and manage a remote workforce. This has increased the methods and amount of outside access into corporate networks to complete work-related tasks. Often, even personal computers and devices are being used now. The sudden change could not easily inculcate appropriate online behavior while working remotely, resulting in many individuals engaging in browsing social media, shopping, and streaming entertainment with the same devices. Since most of these personal devices lack endpoint protection and desktop security, they’re far more vulnerable to malware.
The pandemic immediately forced most companies to figure out how to build and manage a remote workforce. This has increased the methods and amount of outside access into corporate networks to complete work-related tasks. Often, even personal computers and devices are being used now. The sudden change could not easily inculcate appropriate online behavior while working remotely, resulting in many individuals engaging in browsing social media, shopping, and streaming entertainment with the same devices. Since most of these personal devices lack endpoint protection and desktop security, they’re far more vulnerable to malware.
The modern malware is sophisticated and can spread indirectly via unconventional attack devices like routers, tablets, gaming, and entertainment systems connected to the home network or via IoT devices like smart doorbells, cameras, and thermostats. Attackers can easily take advantage and gain access to systems that were never intended for the public. The remote work required by COVID-19 has amplified security vulnerabilities to critical infrastructure as well. Particularly as operations become more remote, it may augment these breach opportunities—often because workers do not have proper security built into home networks and connected devices.
Experts also note that ransomware has targeted applications and data rather than IoT device hardware. In the third quarter of 2020, Check Point Research reported a 50% increase in the daily average number of ransomware attacks compared with the first half of the year.
As the demand for work from home grows, enterprises tend to increase their cloud presence, virtualization, and digitization of assets. With this, there is a tendency to become more efficient and cost-competitive, and thus standardize systems. Standardization is generally good for business; it allows companies to scale products more quickly and enable back-end systems to interoperate more easily.
However, the downside of standardization is that systematic flaws can more easily increase through systems built on standard building blocks. An example is the Ripple20 code breach, which stemmed from the everyday use of a TCP/IP library with bugs. Many enterprises used this code, rendering the breach associated with its buggy code more widespread.
While IoT adoption solves many business problems, attackers are well-versed in its vulnerabilities. Some examples of attacks on IoT technology include:
- Attacks against medical device suppliers: The FortiGuard Labs threat research team uncovered one attack in which cybercriminals sent an email pretending to request multiple medical devices; this email contained a malicious Microsoft Word attachment. If a recipient opened the attachment, the downloaded files could exfiltrate files from the user’s computer.
- Phishing attempts tied to COVID-19: Scammers have used the pandemic as an opportunity to send malicious emails, including those that appear to be reporting from trusted sources like government agencies and news outlets. Due to a rise in these attacks, the World Health Organization (WHO) was forced to issue a statement, and the UN released an advisory warning for people to be on their guard against similar phishing scams.
IT and OT moved closer together as many companies limited the number of workers on-site and defaulted to more remote monitoring and automation. While this provided benefits for social distancing and even more automated responses to abnormal events, it also merges vulnerable OT systems that are not always updated or patched with more mature IT systems.
Furthermore, data privacy becomes a highly sensitive matter in the event of a pandemic—for example, when it comes to contact tracing. IoT security concerns or vulnerabilities need to be tackled by manufacturers and developers before devices get distributed to healthcare consumers. Consistently addressing these concerns will require a collaborative effort from the economic, legislative, medical, and technology sectors. From a technical perspective, there are already many advancements in place to protect devices or their related software from hacks.
When it comes to the pandemic, we need to address not only the protection of people’s health but save production systems as well. Diligence, awareness, and training on cybersecurity is a crucial need.




