There are specific cases where the usage of a thin client to access the OT system environment, for operation or engineering, can be advantageous when compared to a traditional desktop computer.
Thin clients can simplify the deployment, cybersecurity, and maintainability of OT systems by utilizing remote desktop or virtual desktop solutions in lieu of full-fledged desktop computers.
Introduction
OT systems used in process facilities require one or more operator interfaces and one or more engineering interfaces to operate and monitor the production process.
These interfaces are typically known as operator workstations (OWS) and engineering workstations (EWS), respectively. Sometimes, depending on the OT system capabilities and the end user’s OT system policies, a single workstation can combine both the functionality of an OWS and an EWS. OT system engineers will often refer to workstations as clients.
Traditionally, these workstations are delivered as desktop computers running an operating system and the OT system software necessary to perform operation and/or engineering activities. Additionally, these workstations require software such as anti-virus and productivity applications to fully satisfy the needs of operators and engineers alike.
OT Systems Operation and Engineering Infrastructure Planning
During the planning of the OT system, OT system architects must determine the number of workstations that will be necessary, and their type—OWS or EWS.
The number of workstations per OT system depends on user requirements, such as the number of process units that need to be operated and monitored continuously, the number of operators per process unit, the number of engineers expected to be working simultaneously on the OT system for its configuration, and the geographical distribution of the users and their location, just to name a few.
The following list is an example of the criteria used to determine the location of the workstations:
- Organizational arrangements to promote and facilitate coordination between groups
- Building floor layouts
- Improvement of activities workflow
- Safety and ergonomics
- Physical security of the assets
- Access to resources, such as an internet connection, phone lines, and documentation
The location of the workstations is input information utilized during network topology design and engineering, since it is necessary to determine how many locations require fiber optic cables, patch panels, network switches, Ethernet cables, and so on.
 Image courtesy of Pepperl-Fuchs
Image courtesy of Pepperl-Fuchs
Deployment of OT Systems Workstations
The deployment of a workstation involves the following activities:
- Installing an operating system
- Configuring local accounts
- Joining a domain
- Installing the OT system software
- Joining the OT system platform and syncing the client node with the rest of the OT system
- Installing anti-virus software
- Installing productivity software (for example, Microsoft Office, Adobe Acrobat, and/or AutoCAD)
- Workstation security hardening
- Installing the workstation in its final location
These activities are performed in every workstation of an OT system. Hence, the deployment of workstations can become a complicated and time-consuming task for OT systems with multiple workstations spread across different locations.
Management of OT Systems Workstations
As part of the lifecycle management of the OT systems, all workstations are subject to a maintainability, cybersecurity, update, upgrades, and disposal program.
The core activities involve:
- Installation of operating system updates
- Installation of OT system software updates
- Installation of anti-virus updates
- Installation of productivity applications software updates
- Hard disk storage clean-up
- Activity monitoring and log analysis
- Anti-virus scans
Note: depending on your organization policies and the OT system design, periodic backups may occur on specific workstations, especially if data is stored in the local disk.
Planning and carrying out these repetitive activities can add up significant time spent by employees. If there are no tools available to allow OT system engineers to perform these activities from a central location, then these activities must be performed locally on each computer. In a highly distributed OT system, OT engineers must visit multiple site locations to update every one of these clients.
Cybersecurity of OT Systems Workstations
The cybersecurity protection of the workstations begins with their physical security.
OT systems workstations must be installed in a place that ensures physical protection to prevent an unauthorized user from accessing the workstation components, peripheral ports, and communication ports.
To protect the workstations from unauthorized users, it is common to mount workstations on enclosed racks or place them inside desk cabinets that are lockable and have proper ventilation.
These racks and desks are generally located in rooms, such as server rooms, control rooms, and engineering rooms, that are constantly attended, cleaned, and have restricted access. Using full-fledged desktop computers requires sufficient real estate to accommodate all this equipment.
When installed inside a rack enclosure, each workstation needs to be provided with a keyboard, video, and a mouse extender to connect all the necessary peripherals located at the user workplace.
OT system workstations are subject to end-point cybersecurity. Some of these activities include:
- Protecting/disabling local administrator accounts
- Installation and configuration of anti-virus software
- Installation and configuration of application whitelisting
- Configuration of the software firewall (e.g., Windows Firewall)
- Installation of software patches
- User account control configuration
- Configuration of group policy management (this may vary depending if the workstation is part of a domain or a workgroup)
Some of these activities can be performed from a centralized management console, such as Windows Domain Group Policies, yet not all cybersecurity measures can be activated this way. They will need to be performed locally.
Terminal Servers and Virtual Desktop Infrastructure
Thin clients can simplify the deployment activities listed in the previous section by utilizing an approach based on remote desktop or virtual desktop technologies.
To maximize the benefits from using thin clients, the OT system architecture must be based on terminal servers and/or virtual machines.
A terminal server is a high-end server that is built with powerful hardware specifications that allow it to host all the required software applications and services and make them available to multiple clients over a network connection.
Virtual machines are deployed in an environment called a Virtual Desktop Infrastructure (VDI). VDI is a technology that allows the creation and management of multiple virtual machines hosted by a hypervisor which is installed in one or multiple servers. Each virtual machine is a self-contained replica of a computer that runs in the hypervisor.
Through the usage of a thin client, a user can access the OT system work environment through a secure network connection.
Since all the OT system services are running at the terminal server or virtual machine, thin clients are lightweight computers from a hardware and software perspective, since none of the services must run locally.
Deployment and Cybersecurity Simplification
When compared to the traditional approach to OT system workstations, the benefits of using thin clients reduces the total amount of employee hours necessary. Most activities are only performed at the terminal server or in a template virtual machine. For example:
- Software installation
- Client configuration
- System hardening and cybersecurity
In addition to reducing work hours, implementing thin clients also reduces space requirements. A thin client has a small footprint, and some can be mounted behind monitors, using a VESA kit, for example.
 Thin client mounted in the back of a monitor
Thin client mounted in the back of a monitor
Some thin clients have a rugged design, which allows them to be placed in harsh or dirty environments without requiring any extra protection from the environment. Some rugged thin clients are even fanless and can be mounted on DIN rails.
End-point cybersecurity is also simplified because thin clients do not run any kind of services that establish direct communication with OT system servers or OT networks. The thin clients have a dedicated network VLAN that isolates them from any other network when using shared network infrastructure.
System hardening and cybersecurity is implemented at the terminal server or the virtual machines, reducing employee hours dedicated to these activities.
Zero Clients
A zero client is an ultra-light computer that doesn’t run any kind of operating system and doesn’t have any storing capability when compared with a thin client.
A zero client runs a firmware that allows the user to establish a remote network connection to a server to access the computer environment.
The key difference is that zero clients are built around specific communication protocols to establish a connection to the VDI.
Upgrades and Disposal
Like most computer assets, traditional workstations reach obsolescence within three years. This means that desktop computers have a short lifecycle of support from the manufacturer.
When used in OT system environments, however, workstations tend to be used for long periods of time—well beyond the hardware end of life.
Thin clients and zero clients are not part of the OT system lifecycle. Activities related to OT system software upgrades, which also include operating system updates, anti-virus updates, and so on, do not need to be performed on thin clients or zero clients.
OT system engineers can focus on the core infrastructure during system updates and upgrades, leaving the thin clients and zero clients untouched.
Thin clients and zero clients simplify scaling up the number of workstations if necessary in a much faster and more cost-effective way, when compared to desktop computers.
Selecting Thin Clients and Zero Clients
As mentioned before, thin clients and zero clients are best deployed in server-based environments such as a terminal server or VDI, so this should be the first thing to consider.
A few things to consider when selecting thin clients or zero clients:
- Number of video output ports (dual or quad)
- Type of video output ports
- Number of network ports
- Mounting capabilities
- Communication protocols supported
- Power supply requirements
- Ruggedness of the design
Some advanced feature that are worth considering are:
- Support of a thin client management tool to expedite thin client configuration and management (IP address, allowed remote connections, session monitoring, etc.)
- Firmware/BIOS level security (boot protection, external storage drive deactivation, etc.)
- Additional user authentication security (2FA or MFA)
- Specific plugins and compatibility with the OT system
OT System Considerations
When deploying thin clients or zero clients, be aware of any limitations that the OT system may have.
It is not enough to simply confirm that the OT system supports usage of thin clients. It is necessary to fully understand the limitations in terms of performance, such as number of active remote sessions allowed, response rate of process graphics, redundancy capabilities, and so on.
Deployment of thin clients does not necessarily reduce the number of licenses required per session. Verify licensing terms with the OT system vendor. Consider software licenses, operating system remote session licenses, productivity application licenses, and so on.
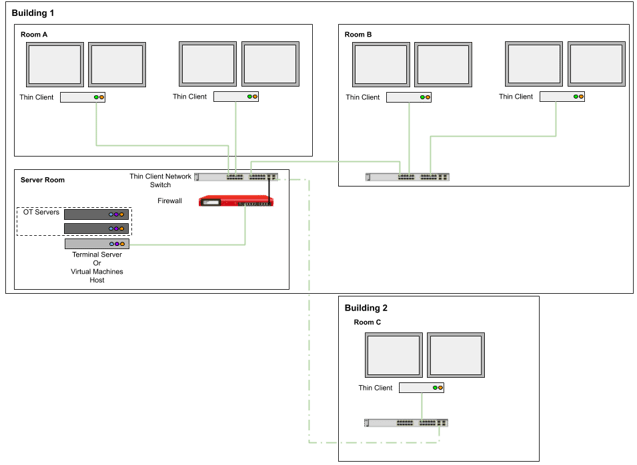 Benefits of thin clients are maximized in remote desktop or virtual machine environments. Consult OT system vendors about their supported architectures.
Benefits of thin clients are maximized in remote desktop or virtual machine environments. Consult OT system vendors about their supported architectures.
Conclusion
Thin clients and zero clients have been used extensively for decades, but they haven’t set a foothold in OT systems architecture yet—primarily because of lack of information, and because OT systems are still designed based on fat clients (meaning full-fledged desktop computers).
An OT system based on thin clients brings deployment flexibility, reduces its footprint, simplifies cybersecurity, and lowers the total cost of ownership of the OT system. Thin clients and zero clients are great solutions when installed in remote locations that are mostly unattended, and in locations with harsh or dirty environments.
Their deployment cannot be taken lightly. Therefore, collaboration with the OT vendor and thin client manufacturer is necessary for a successful implementation.
Interested in reading more articles like this? Subscribe to ISA Interchange and receive weekly emails with links to our latest interviews, news, thought leadership, tips, and more from the automation industry.




