In today's connected world, securing industrial control systems (ICSs) is more important than ever. Industrial control system cybersecurity standards like NERC CIP, ISA-99 (IEC-62443), and NIST 800-82 have been drafted to assist in identifying and implementing ICS security best practices.
There are three common aspects that these standards and many cybersecurity experts agree are fundamental to deploying secure industrial networks.
Network architecture: From a network architecture standpoint, deploying a defense-in-depth approach that incorporates secure zones and conduits is the foundation of secure industrial network design. From a practical standpoint, it is rapidly becoming a requirement to design for reliable secure remote access.
Secure device configuration: With today's converged networks, proper configuration of industrial network devices is becoming more complex, and security features are often left disabled for convenience. This leaves ICS networks vulnerable to not only malicious attacks, but also inadvertent breaches.
Network security management: A good network security management system will not only help you deploy and enforce security policies throughout your ICS network, it will also allow you to monitor and log network events while providing real-time notification of security events.
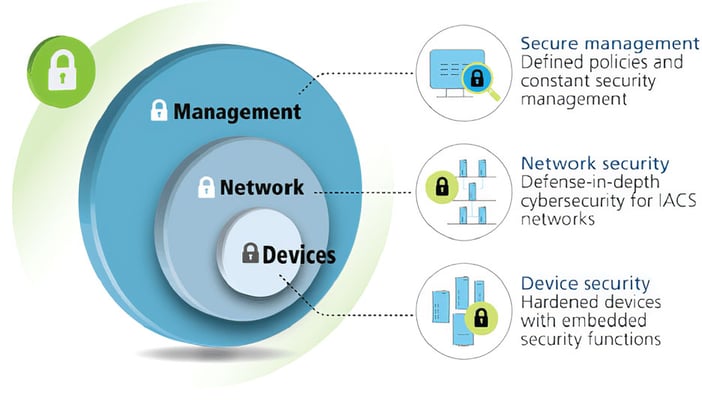 Figure 1. Security layers
Figure 1. Security layers
Security-minded network infrastructure
When designing an ICS network, today's best practice is to deploy a defense-in-depth security architecture (figure 2), which segments network traffic into defined zones, and then limits communications between these zones to only predefined traffic. This architecture allows reliable, timely communications within these zones and limits the potential scope of a breach in any particular zone. There are three steps to designing a defense-in-depth architecture.
Step 1: Network segmentation
Network segmentation involves breaking down the network into physical or logical zones with similar security requirements. The benefit of segmenting the network is that each section can focus specifically on the security threats that are posed to that section of the ICS. Deploying the segmentation approach is advantageous, because each device is responsible for a particular segment of the network, as opposed to being responsible for the security of the entire ICS.
Step 2: Define zone-to-zone interactions
Once you define the specific traffic that needs to pass between secure zones, unauthorized traffic can then be filtered using industrial firewalls. A general best practice is to whitelist the traffic that needs to flow between each zone and block all other traffic. Industrial firewalls typically have deep packet inspection to filter industrial protocols at a more granular level than traditional firewalls. Many industrial firewalls also have a transparent mode that allows you to install them into existing networks without having to reconfigure the network IP scheme.
When connecting ICS networks to enterprise information technology networks or the Internet, another best practice is to create a demilitarized zone (DMZ) with an industrial firewall. With a DMZ, there is no direct connection between the secure ICS network and the enterprise network, but the data sever is still accessible by both. Eliminating a direct connection between the ICS and enterprise networks significantly reduces the possibility of unauthorized traffic passing to different zones, which could jeopardize the security of the entire network.
Step 3: Support secure remote access on industrial networks
Finally, within the industrial automation and control system industry there is a growing need for access to remote sites for monitoring or maintenance. This significantly increases the risk of someone with malicious intent accessing the network. Networks that require the remote site to be constantly connected to the ICS should use a virtual private network (VPN) that supports a secure encryption method, such as IPsec or OpenVPN, which does not allow unauthorized users to access the network. There are three main advantages of using a VPN. The first is that the data is encrypted when it is transmitted. The second is that it forces the sender and recipient to authenticate who they are, so that data is only passed between verified devices. The third is that by enforcing encryption and authentication, you can ensure the integrity of the data.
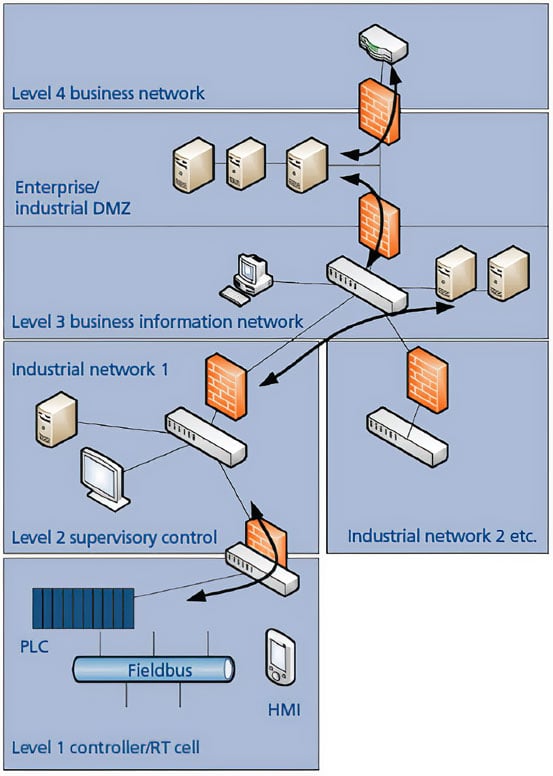 Figure 2. Security zones
Figure 2. Security zones
Secure device configuration
Once you have a well-designed network architecture, you need to make sure that the switches and other network devices are configured to match your security requirements. This can be daunting for a control engineer who does not have deep networking expertise. Luckily, the IEC 62443 standard provides guidance by defining some of the key features you will want on your switches and other devices. Below are the seven functional requirements defined by the standard, along with a brief explanation of their relevance.
- Identification and authentication control: Public key authentication should be used to secure server-to-device and device-to-device connections. To ensure identification and authentication control, each network device must be able to validate security certificates by checking the authentication of the signature, as well as the revocation status of a certificate.
- Use control: Every device that appears on a network must support login authentication. To restrict unauthorized users from gaining access to devices or the network, the application or device must limit the number of times a user can enter the password incorrectly before being locked out.
- Data integrity: Across all ICS networks, the integrity of the data is very important for ensuring that data is accurate and that it can be processed and retrieved reliably. There are several security measures you can use to protect the data, including SSL, which supports encryption between a Web browser and a server.
- Data confidentiality: When data is stored or transmitted across networks, it has to be safe and secure. The data should be protected from all types of threats ranging from very basic ones to highly sophisticated attacks. Data must be secured at all times from those who wish to eavesdrop on communications, alter settings, or steal data.
- Restrict data flow: One of the most effective methods of restricting the flow of data is to split the network into different zones. Each zone uses specific security features so that only those with authorization can access and send data from a specific zone. Another benefit is that if a zone is infiltrated, the threat cannot easily spread to other parts of the network, which helps limit the damage caused by the security breach.
- Timely response to events: It is essential that system operators are able to respond quickly to security incidents that occur on the network. To facilitate this, the network must support the features needed to alert system operators if a problem occurs and also keep a record of any abnormalities that happen on the network. All network events should be processed in real time or at least fast enough for system operators to respond in time to prevent further damage to the ICS network.
- Network resource availability: Devices on ICS networks must be able to withstand denial-of-service attacks from people with only a basic understanding of ICS networks or who are presented with an opportunity due to operator error. Devices must also be able to withstand attacks from entities that have high motivation and high levels of ICS-specific skills. The important point is that the network must not experience downtime regardless of who is attacking the network.
Now that the security configuration requirements have been outlined, we will discuss three common vulnerabilities and how properly configured network devices helps protect your ICS.
Vulnerability #1: Use of default device passwords: Strong password-based authentication is a fundamental requirement for network security, yet many devices on industrial networks still use default passwords shipped from the manufacturers. Although this may be convenient for maintenance, it leaves your network extremely vulnerable. To address this security issue, the devices located on industrial networks must enforce strong password policies that include a minimum password length and a variety of character types. As they are much harder to guess, passwords that adhere to a strong password policy will help protect against brute force attacks.
Vulnerability #2: Plain text transmission of user and passwords: Many devices on ICS networks still use nonsecure plain text communications when users log in to configure them. This makes it easy for someone "sniffing" the connection to obtain the user ID and password information to further access and exploit the network. The best way to avoid this is by ensuring the system supports secure communication protocols, such as SSL and SSH, or, alternatively, password protection for device configuration through HTTPS.
Vulnerability #3: Unencrypted backup files: It is common practice to back up network configuration files in case of a failure. Often these files are stored as plain text files on shared or contractor laptops. In the wrong hands, these files can be easily accessed and used to exploit the network. The best practice is to encrypt these configuration files to protect the information they contain.
ISA offers standards-based industrial cybersecurity training, certificate programs, conformity assessment programs, and technical resources. Please visit the following ISA links for more information:
- Cybersecurity Books
- Cybersecurity Training Courses
- Cybersecurity Blog Posts
- Cybersecurity Resources Portal
- ISA Global Cybersecurity Alliance
- IEC 62443 Conformance Certification
- ISA Suite of Security Standards
- ISA Family of Standards
- ISA/IEC 62443 Cybersecurity Certificate Programs
Network security management
Ensuring a secure network does not end with deployment. A good network security management policy needs to ensure that the network remains secure throughout the entire network life cycle. A good network management tool is essential to helping you establish and maintain such a network.
Network deployment
Many network management systems (NMSs) have mass configuration tools, which not only speed deployment, but can also help you consistently configure and deploy network devices. Using wizards or scripting tools is an easy way to make sure your network devices are deployed according to your security policy.
Network operation
Once your network is deployed, a good NMS will help you visualize the health and security of your network, making it easier to monitor and enforce security policies. It also monitors network events in real time to inform you immediately of security concerns. It logs security events, such as successful/unsuccessful login attempts and firewall rule violations, to inform you of attempted or successful breaches and where they are from.
Network maintenance
Throughout the automation system life cycle, local engineers or system integrators often need to perform maintenance. This maintenance typically includes changing, replacing, or updating devices in the network. It is important to note that whenever a device configuration is modified, there is a possibility that it will no longer be secure, and it will become vulnerable to cyberattacks. As ICS networks continuously evolve and change, the network and all the devices located on it must be constantly monitored to ensure that the designed security policies are enforced over time.
It is also good practice to deploy the security patches that network device manufacturers make available to address new vulnerabilities as they are discovered. Organizations like ICS-CERT track known vulnerabilities for industrial control devices and work with manufacturers to develop and communicate these patches. When selecting ICS components, see how quickly the manufacturer typically responds to vulnerabilities when they are discovered.
Ongoing attentiveness
Securing a network and the devices installed on it is not easy. The threats posed to industrial networks constantly change and evolve. To protect the network as well as possible, system operators should adopt the defense-in-depth network architecture. Aside from a good overall network design, system operators should select hardened devices that support more advanced security features, such as those mentioned in the IEC 62443 standard. Overall, system operators should have a thorough understanding of the possible threats facing their network, as well as detailed knowledge of the best practices for designing and maintaining networks. Finally, ensuring that the network is constantly monitored throughout the network life cycle will mitigate any security risks that arise as the network evolves.
A version of this article also was published at InTech magazine.




