This article was written by Bill Lydon, InTech magazine’s chief editor.
Cybersecurity is now becoming a high priority for industry and the government, but the Automation Federation (AF) and its sister organization the International Society of Automation (ISA) have been ahead of this recent industry and government activity.
The partners have been working with hundreds of end user and vendor members on industrial cybersecurity best practices, methods, standards, and certifications during the last seven years. This is not surprising, because members are stewards of a wide range of important facilities, including utilities, power grids, pipelines, and manufacturing, chemical, food, pharmaceutical, and petrochemical plants around the world.
Cyberattacks on industrial operations continue to be a great concern, but at the same time, management is increasingly demanding real-time communications between automation and business systems. In addition, the decreasing number of experienced automation experts is driving the need for remote plant operations over the Internet, raising vulnerability concerns.
The risks of cyberattacks are growing and present serious threats to the health and well-being of our citizens’ economic and national security. These attacks have the potential to disrupt or halt national power grids, transportation, telecommunications systems, financial networks, manufacturing, and government functions. The Automation Federation and ISA activities have been expanding and accelerating based on informed strategies put into action with ongoing initiatives, including ISA99, ISA Security Compliance Institute, and ISASecure® .
More visibility has been given to cybersecurity in the U.S. with the U.S. Presidential Executive Order 13636, announced in President Obama’s 2013 State of the Union address and signed on 12 February 2013 to confront the growing threats and risks of destructive and potentially deadly cyberattacks on the nation’s critical infrastructure. The executive order (EO) calls for the development of a national cybersecurity framework that includes “standards, methodologies, procedures, and processes that align policy, business, and technological approaches to address cyberrisks,” and “help owners and operators of critical infrastructure identify, assess, and manage cyberrisk.”
The National Institute of Standards and Technology (NIST) of the U.S. Department of Commerce is charged with developing the framework. The AF and ISA have been engaged and are a knowledgeable industrial automation and control system (IACS) resource. Describing the progress on cybersecurity, former ISA president Leo Staples, who has been involved in these activities, commented, “Since 2008 the Automation Federation has delivered a consistent message regarding the vulnerability of industrial automation and control systems to cyberattacks and the importance of protecting those systems against such attacks. Our efforts to deliver this message have proven fruitful and are now recognized by members of Congress, DHS [Department of Homeland Security], NIST, and the White House. In a few short months, NIST will issue the draft of the Framework of Cybersecurity Standards. At that point, the real work will begin as the draft is disseminated and ultimately adopted across the various industry sectors. NIST and the White House have also called on the Automation Federation to assist in the implementation of the cybersecurity framework.”
NIST Cybersecurity Framework Workshop
The Automation Federation and ISA participated in a Cybersecurity Framework Workshop conducted at the University of California San Diego, La Jolla, Calif., on 10-12 July. The AF and ISA participants in the workshop included Eric Cosman, co-chair of the ISA99 standards development committee, and Steve Mustard, member of the AF government relations committee. The purpose of the workshop was to discuss, refine, and generate content for the cybersecurity framework, with a focus on core elements and incorporating cross-sector needs.
The first Cybersecurity Framework Workshop was held at the offices of the U.S. Department of Commerce in Washington, D.C., on 3 April. Attendees included Leo Staples, 2013 AF energy committee chair; Eric Cosman; Johan Nye, chairman, governing board of the ISA Security Compliance Institute; Steve Mustard; and Mike Marlowe, AF managing director and government relations director. The workshops are part of a 240-day process to produce a preliminary framework for industry to use. The 4th Cybersecurity Framework Workshop was held 11-13 September 2013 at The University of Texas at Dallas.
The framework offers a way to take a high-level, overarching view of an organization's management of cybersecurity risk by focusing on key functions of an organization's approach to this security. The high-level functions are labeled know, prevent, detect, respond, and recover. These are broken down further into categories. For instance, the "prevent" category includes identity and access management, physical security, training, and awareness. It is important to note that NIST personnel have gone to great lengths to emphasize that they are not chartered to develop any new standards but to reference industry standards. ISA has cybersecurity standards that can easily support the objectives of the executive order. NIST will release a preliminary framework for public comment in October 2013 and the final framework in February 2014.
Leadership perspective
The Automation Federation managing director Mike Marlowe discussed recent activity: "The Automation Federation continues to be engaged in the important work underway by NIST to complete the creation of the Framework of Cybersecurity Standards. We continue to provide input regarding the inclusion of language in the framework that allows the industry sectors to protect the industrial automation and control systems, which are vital to the safety and security of our country. At the request of NIST, the Automation Federation is also assisting in the organization of follow-up meetings to discuss the framework after the draft is released in October. We are committed to helping NIST complete the work of building the framework."
Incentives to support adoption
Michael Daniel, special assistant to President Obama and the cybersecurity coordinator, wrote on The White House Blog (www.whitehouse.gov/blog/) on 6 August 2013 about the possibility of incentives for companies to join a cybersecurity program that is under consideration (www.whitehouse.gov/blog/2013/08/06/incentives-support-adoption-cybersecurity-framework). He wrote, "While the set of core practices have been known for years, barriers to adoption exist, such as the challenge of clearly identifying the benefits of making certain cybersecurity investments. As directed in the EO, the Departments of Homeland Security, Commerce, and Treasury have identified potential incentives and provided their recommendations to the president, through the assistant to the president for homeland security and counterterrorism and the assistant to the president for economic affairs." Some of the recommended incentives he cites are cybersecurity insurance, grants, public recognition, and cybersecurity research. These are only ideas and do not yet represent a final administration policy. Some incentives would require legislative action to put in place.
ISA cybersecurity initiatives
In response to a NIST open request for information on the cybersecurity framework, the Automation Federation submitted comprehensive responses in early April from both the ISA99 standards development committee and the ISA Security Compliance Institute (ISCI). ISA99 and ISCI have been developing IACS multi-industry consensus standards and conformity assessment programs, respectively, to protect vital industrial and critical infrastructure. The application of automation to increase productivity, reduce costs, and share information in real time across multiple industrial and enterprise systems is vital to maintain and increase industrial competitiveness. To meet industry competitiveness objectives and protect IACS from cyberthreats, the NIST cybersecurity framework, like the ISA99 standards, is intended to apply across multiple industry sectors. These are the major cybersecurity initiatives:
ISA99 committee
The ISA99 standards development committee brings together more than 500 industrial cybersecurity experts from multiple industries and applications to develop the ISA-62443 series of American National Standards on IACS security. These standards are a framework for companies to achieve and maintain security improvements through a life cycle that integrates design, implementation, monitoring, and continuous improvement. This original and ongoing work is being adopted by the Geneva-based International Electrotechnical Commission (IEC) as the IEC 62443 series (see the section "Overview" for more information on the ISA-62443 series).
ISA Security Compliance Institute
The ISA Security Compliance Institute, a subsidiary of ISA, manages the ISASecure® program, which recognizes and promotes cybersecure products and practices for industrial automation suppliers and operational sites. The ISASecure designation is earned by industrial control suppliers for products that demonstrate adherence to ISCI cybersecurity specifications derived from open, consensus industry standards. ISASecure certifications evaluate product/system cybersecurity characteristics, laboratory test products/systems, and assess suppliers' adherence to cybersecurity life-cycle development best practices. ISCI develops industrial automation control systems certifications, which assess conformance to the ISA-62443 standards and reference other relevant international standards, such as IEC 61508 and IEC 61511 for safety-instrumented systems, as appropriate to the particular certification program. ISCI has committed to maintaining alignment of ISASecure certification requirements to the ISA-62443 series of standards.
Test lab accreditation assures users of the competence and impartiality of the certification body being accredited. ISASecure is an ISO/IEC Guide 65 conformance scheme. As such, all ISASecure certification bodies (test labs) are independently accredited to ISASecure requirements, ISO/IEC Guide 65, and ISO/IEC 17025 by an ISO/IEC 17011 accreditation body, such as ANSI/ACLASS, the Japan Accreditation Bureau (JAB), and other country-specific ISO/IEC 17011 accreditation bodies.
ISASecure Embedded Device Security Assurance (EDSA) is a certification program for embedded devices, which are special-purpose devices running embedded software designed to directly monitor, control, or actuate an industrial process. The ISASecure EDSA certification program is currently available, and several suppliers' devices have been certified to ISASecure Security Level 1 or 2. EDSA will certify device compliance to the ISA-62443-4-2 cybersecurity standard.
ISASecure System Security Assurance (SSA) is a certification program for industrial automation and control systems. The certification tests and assesses for compliance to the ISA-62443 standards. The primary focus of the SSA program is to certify compliance to the ISA-62443-3-3 cybersecurity standard. The ISASecure SSA certification program is currently under development and is expected to be released in the fourth quarter of 2013.
ISASecure Security Development Life-cycle Assurance (SDLA) is a certification program to assess the supplier's product development process to ensure it incorporates a security development life cycle and will certify to the ISA-62443-4-1 cybersecurity standard. The ISASecure SDLA certification program is currently under development and is expected to be released in the fourth quarter of 2013.
Reflecting international concerns about IACS security, in May 2013 the Japan Information Technology Promotion Agency (IPA) dedicated an industrial automation and control test lab called the control systems security center (CSSC) in Sendai, Japan (www.css-center.or.jp/en/index.html). The IPA has adopted ISASecure as part of the Japanese critical infrastructure protection scheme and has translated the ISASecure EDSA certification requirements into Japanese for use by the CSSC, suppliers, and asset owners in Japan. The CSSC is currently undergoing accreditation to the ISASecure conformance scheme by the JAB and is expected to begin ISASecure certification testing in the first quarter of 2014. The ISASecure SSA and SDLA specifications will also be translated into Japanese as they are completed in English in 2013.
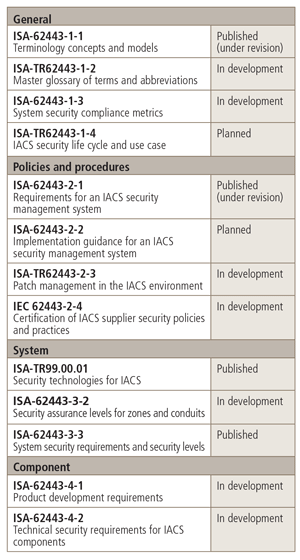
ISA99 plan overview
The figure provides a quick overview of all the work products (standards, technical reports, etc.) available, under development, or planned by the ISA99 standards development committee.
Each element of the work plan has three separate numerical designations. Originally, all work products of the committee were numbered in the series ISA-99.xx.yy, and this terminology is still in common use. More recently, there was a decision to more closely align ISA's efforts with those of the corresponding IEC Technical Committee 65, Working Group 10, which is responsible for delivering a series of international standards designated as IEC 62443-x-y. As part of the plan to harmonize the numbering of ISA and IEC standards, the ISA work products are being renumbered from ISA-99.xx.yy to ISA-62443-x-y. The new numbers will appear as each document is released or rereleased.
Other activity
The ISA99 committee continues to develop additional standards and technical reports in the ISA-62443 (IEC 62443) series, several of which will soon be circulated for review and comment. More information is available on the wiki at the ISA99 website (www.isa.org/isa99). ISA offers a number of training courses on industrial cybersecurity and is currently developing a certificate program in cybersecurity.
ISA99 and the U.S. government cybersecurity framework
The Automation Federation and ISA are strongly advocating the inclusion of the ANSI/ISA99, Industrial Automation and Control Systems Security standards (IEC 62443) within the U.S. government's cybersecurity framework. Because they apply to all key industry sectors and critical infrastructure, ANSI/ISA99 standards represent a comprehensive approach to cybersecurity.
Putting widespread cybersecurity standards in place is vital, because many of the U.S.'s industrial production settings and infrastructure environments are woefully underprepared to address cyberwarfare. If industrial control systems and critical infrastructure-such as a power plant, water treatment facility, or transportation grid-are attacked, the result could be significant equipment impairment, production loss, regulatory violations, environmental damage, and public endangerment.
The development of a national cybersecurity framework is a significant first step in addressing the country's cyberrisks and helping owners and operators of critical infrastructure identify, assess, and manage cyberthreats.
- AF responded to two requests for information (RFIs) on 24 April to NIST on behalf of the ISA99 committee and the ISA Security Compliance Institute for the cybersecurity framework. Both RFIs focused on the industrial automation and control systems as part of the framework.
- On 27 June, AF and ISA leaders took part in a telephone conference with NIST staff to discuss the Cybersecurity Framework Workshop, which was held 10-12 July in San Diego, Calif.
- NIST has requested help from AF in identifying a location for a "deep dive" review of the framework draft once it is released in October. AF and NIST staff are working on the details.
The Automation Federation and ISA will continue to take active roles in automation industry cybersecurity, including the creation and refinement of the U.S. cybersecurity framework.
ISASecure Embedded Device Security Assurance Certification |
| Industrial control suppliers earn the ISASecure™ designation for products that demonstrate adherence to an industry consensus cybersecurity specification for security characteristics and supplier development practices. The first ISASecure certification, Embedded Device Security Assurance (EDSA), focuses on the security of embedded devices and addresses device characteristics and supplier development practices for those devices and will meet requirements of ISA-62443-4-2 when available. An embedded device that meets the requirements of the ISASecure EDSA specification earns the ISASecure EDSA certification. It is a trademarked designation that provides instant recognition of product security characteristics and capabilities and provides an independent industry stamp of approval similar to a "Safety Integrity Level" Certification (ISO/IEC 61508).
The ISASecure EDSA certification offers three levels of recognition for a device, reflecting increasing levels of device security assurance. The levels are ISASecure Level 1 for Devices, ISASecure Level 2 for Devices, and ISASecure Level 3 for Devices. All levels of security certification granted under this program contain the following technical elements:
FSA and SDSA evaluation requirements increase in rigor for Levels 2 and 3, while CRT criteria are the same regardless of certification level. The ISASecure Embedded Device Security Assurance Certification brochure, available at www.isasecure.org, describes the three technical certification elements, certification levels, and the certification program.
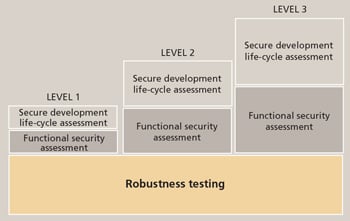 ISASecure technical certification elements ISASecure technical certification elements
|
 About the Author
About the Author
Bill Lydon is InTech’s chief editor. He has more than 25 years of industry experience in building, industrial, and process automation, including product design, application engineering, and project management. Contact Bill at blydon@isa.org.
A version of this article also was published at InTech magazine.




