With the increasing prevalence of high-profile cyberattacks and security breaches, these events may seem unavoidable. The consequences, however, come at a tremendous cost to businesses and consumers. More alarming is that the intent of cyberattacks has gone beyond stealing personal and financial data and now includes extortion, destruction of intellectual property, and damage to critical infrastructure.
Cybercriminals are becoming more aggressive and sophisticated in their attacks. As noted in one security threat report, exploit kits evolve "to stay one step ahead of security systems, with greater speed, heightened stealth, and novel, shape-shifting abilities.”
Protecting critical infrastructure
In the U.S., the potential for a cyberattack on critical infrastructure is a growing concern. In the U.S., the Obama administration issued Presidential Policy Directive (PPD)-21 – Critical Infrastructure Security and Resilience. The directive states, “The nation’s critical infrastructure provides the essential services that underpin American society. Critical infrastructure must be secure and able to withstand and rapidly recover from all hazards.” Those hazards include cyberthreats. Presidential Executive Order 13636 – Improving Critical Infrastructure Cybersecurity was released in conjunction with PPD-21 to specifically deal with the cyberthreat to critical infrastructure. Per the executive order, “The cyberthreat to critical infrastructure continues to grow and represents one of the most serious national security challenges we must confront. The national and economic security of the United States depends on the reliable functioning of the Nation’s critical infrastructure in the face of such threats.”
OT security
A key component in protecting critical infrastructure from cyberattack is protecting the automated systems used to monitor and control critical processes. Systems that control water and wastewater processes are known by many names. Industrial control systems, supervisory control and data acquisition, distributed control systems, and industrial automation and control systems (IACSs) are just a few of the terms that fall under the general category of operational technology (OT).
Attacks on OT systems and networks are becoming more common. Although some high-profile attacks on critical infrastructure have been reported, we do not know the full extent, because cyberattacks do not have to be reported unless there is a breach of personal information or financial data.
Because we do not hear of many attacks on critical infrastructure, some people assume the cyberthreat to OT is not a great concern. We might not know the actual number of attacks, but we do know that malware has been developed specifically to attack critical infrastructure (e.g., Stuxnet and Black Energy). In December 2015, for example, an attack on the Ukrainian power grid left hundreds of thousands without power. These attacks are a powerful reminder that the threat to critical infrastructure cannot be ignored.
NIST cybersecurity framework
Executive order 13636 directed the National Institute of Standards and Technology (NIST) to develop a cybersecurity framework to reduce risk to critical infrastructure. The intent of the framework was to provide critical infrastructure owners and operators a flexible and repeatable approach to meeting baseline cybersecurity measures and controls. In February 2014, NIST released its Framework for Improving Critical Infrastructure Cybersecurity Version 1.0. Click this link to get more information on the NIST framework.
The cybersecurity framework (CSF) is a voluntary, risk-based approach for managing cybersecurity risks for critical infrastructure. It references industry standards, guidelines, and best practices known as informative references to help organizations manage cybersecurity risks.
The water sector does not currently have specific directives for securing OT, so the CSF is a useful resource for identifying relevant resources. The CSF is not meant to replace an existing program, but can be used as the foundation for a new cybersecurity program or to improve an existing program. The framework consists of three parts: the implementation tiers, the framework profile, and the framework core (figure 1).
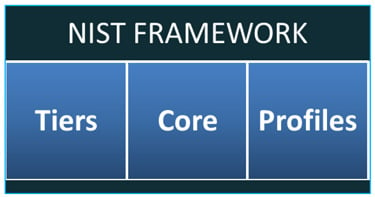 Figure 1. NIST Cybersecurity Framework
Figure 1. NIST Cybersecurity Framework
Framework implementation tiers define the organization’s risk management practices by one of four tiers. Tier 1 represents the least amount of risk management, and tier 4 the most. Each organization must determine which tier is appropriate for it, given the organization’s unique goals, feasibility of implementation, and acceptable level of cybersecurity risk.
The framework profile helps an organization define a road map for moving from a “current” profile that defines current risk management practices, to a “desired” profile that defines the outcomes needed to achieve the desired cybersecurity risk management goals. Comparing the current profile to the desired profile produces a gap analysis that can be used to establish a plan defining actions required to meet organizational goals, and to prioritize activities for cost-effective allocation of resources.
The framework core is a set of cybersecurity activities, desired outcomes, and applicable references common across all critical infrastructure sectors. They are segmented into five functions (figure 2). These functions organize basic cybersecurity activities at their highest level. The five functions are identify, protect, detect, respond, and recover.
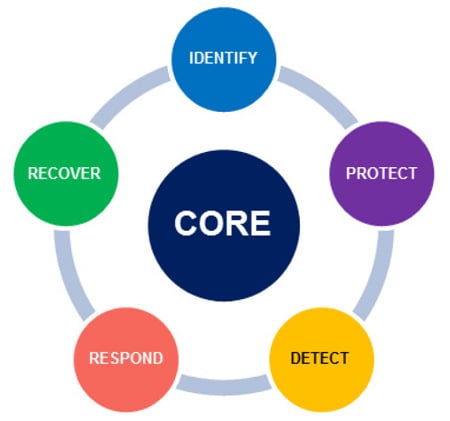 Figure 2. The framework core
Figure 2. The framework core
Figure 3 shows how a function (identify) is broken down into various categories (asset management for this example). Categories are broken down into subcategories (physical devices and systems inventoried), leading to specific informative references, such as the ISA-62443 standard. Additionally, the specific section of the informative reference associated with the subcategory is provided to clearly identify the content most relevant to that subcategory.
The informative references listed by the CSF are not mutually exclusive, but complement one another. One resource is likely to provide more detailed guidance than another on a particular aspect of cybersecurity. As a result, all relevant resources should be considered when developing or updating a security plan.
ISA-62443 is one of the key standards referenced in the CSF. ISA developed this multipart standard for OT security. The standard provides a flexible framework for developing a comprehensive security plan for critical infrastructure entities such as water and wastewater utilities.
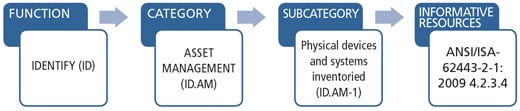 Figure 3. Linking cybersecurity function to informative references
Figure 3. Linking cybersecurity function to informative references
One particularly important section is ANSI/ISA-62443-2-1, Security for Industrial Automation and Control Systems Part 2-1: Establishing an Industrial Automation and Control Systems Security Program, which is aimed at asset owners and operators responsible for establishing and managing a utility’s cybersecurity program. Unlike other security standards that cover only technical considerations for cybersecurity, ISA-62443-2-1 focuses on the critical elements of a security plan relating to policies, procedures, practices, and personnel. It is a valuable resource to management for establishing, implementing, and maintaining a utility-wide security plan.
The first step in developing an OT security program as defined by ISA-62443-2-1 is risk analysis, starting with the business rationale for cybersecurity. As noted in the standard, “Establishing a business rationale is essential for an organization to maintain management buy-in to an appropriate level of investment for the IACS cybersecurity program.”
Why a business case?
A well-defined business case for automation cybersecurity is essential for management buy-in to ensure the long-term allocation of resources needed to develop, implement, and maintain a utility-wide cybersecurity program for the OT controlling critical infrastructure. Without a strong commitment by senior management, utility personnel will find it difficult to prioritize the allocation of resources—especially when faced with resource-intensive challenges such as aging infrastructure.
The business rationale for cybersecurity is based on the potential impact that a cybersecurity event can have on public health and safety, the environment, business continuity, emergency preparedness, regulatory compliance, and the public’s confidence in the utility. Developing a business rationale for cybersecurity identifies the business reasons for investing in cybersecurity to lower risk and protect the utility’s ability to perform its mission.
Cybersecurity is not an absolute, but a matter of degree. Because most water/wastewater systems have limited funding and personnel, mitigating all threats is not feasible or practical. By defining a business rationale for OT cybersecurity, executive management can define acceptable levels of risk for the utility, so that utility personnel can better understand the priorities to address in the security plan. By determining the cost-benefit aspects of security measures, the utility will get the maximum results from the money spent. Not having a well-defined security plan results in inefficient use of limited resources and can create a false sense of security.
When analyzing the business rationale, executives may find economic benefits similar to those of worker safety and health programs. Each year, workplace deaths and injuries cost U.S. businesses tens of billions of dollars. The Occupational Safety and Health Administration reports that employers save $4 to $6 for every $1 invested in an effective safety and health program.
Similarly, each year security breaches cost businesses billions of dollars in fines, litigation, and lost customers. According to the Ponemon Institute’s 2016 Cost of Data Breach Study, the average cost of a data breach is $4 million, a 29 percent increase since 2013. However, an attack on a critical water or wastewater system could have significant consequences that far exceed the monetary costs. A cybersecurity event that negatively impacts operations could expose a utility to litigation affecting business continuity and its ability to carry out its mission.
OT security is also fundamental to the creation of a culture of security within the utility, as noted in the American Water Works Association (AWWA) standard ANSI/AWWA G430-14 – Security Practices for Operation and Management. A key directive of the standard is an “explicit and visible commitment of senior leadership to security.” The AWWA G430-14 standard addresses the broad issues of security, and protecting operational technology is a key facet of security. An established business rationale for OT cybersecurity shows that management takes its commitment to security seriously. Cybersecurity must become a fundamental component of the utility’s culture, just like safety.
Should I worry about a cyberattack?
The probability of a state-sponsored cyberattack on a utility is most likely extremely low. However, water and wastewater utilities might be viewed as easy targets by radicalized, lone-wolf threat actors. “Security by obscurity” is no longer an option for small and medium utilities that have not considered external threats a concern in the past.
However, attacks make up only a small part of cyberthreats, as most originate internally. Whether malicious or accidental, the utility’s goal should be to prevent or minimize any type of cybersecurity event that will affect the availability and reliability of a critical system. A comprehensive security plan recognizes and prepares for both intended and unintended cybersecurity events. This will ultimately enhance the utility’s overall security and minimize any negative consequences on business continuity.
IT’s job?
Many in the OT world assume that their information technology (IT) department is handling the cybersecurity plan. IT professionals, who are responsible for ensuring the availability, integrity, and confidentiality of business and enterprise networks, are important members of a cross-functional team that develops and implements a utility-wide cybersecurity plan. However, the responsibility for protecting OT systems and networks—and the critical infrastructure they control—from a cybersecurity event lies with those who operate and maintain those networks.
An established cybersecurity business case will clearly define security roles and responsibilities for all utility personnel, including those involved with emergency preparedness and business continuity.
 Figure 4. High-profile cyberattacks and security breaches are reminders that a comprehensive security plan is needed to protect industrial control systems and the critical infrastructure they control. A well-defined business case for automation cybersecurity will ensure management buy-in and long-term allocation of resources.
Figure 4. High-profile cyberattacks and security breaches are reminders that a comprehensive security plan is needed to protect industrial control systems and the critical infrastructure they control. A well-defined business case for automation cybersecurity will ensure management buy-in and long-term allocation of resources.
Guidance for developing a business case
A useful feature of ISA-62443-2-1 is annex A, which provides guidance on developing all elements of the cybersecurity management system as defined in the standard. Annex A includes helpful information for applying the standard and tailoring it to the organization’s specific needs. Although it is not a step-by-step process, it does offer useful guidance in developing each element, including the requirement for a business rationale.
Per annex A, there are four key components of a business rationale: prioritized business consequences, prioritized threats, estimated annual business impact, and cost of countermeasures.
Prioritized business consequences: For a water or wastewater utility, there are numerous areas where a cybersecurity event could cause significant negative consequences for operations. Those areas include public health and safety, the environment, business continuity, emergency preparedness, regulatory compliance, and public confidence in the utility to fulfill its mission. It is likely there will be compelling business reasons for ensuring that the consequences of a cybersecurity event—intended or otherwise—are not realized.
Prioritized threats: As stated previously, it is neither practical nor feasible to fully mitigate all risks. Limited resources demand that the most credible threats be given priority for developing mitigation strategies and allocating resources effectively. Unfortunately, there are many events that can negatively affect operations, from disgruntled employees to radicalized, lone-wolf threat actors, to common technical defects. By prioritizing threats in the business rationale, it will be clear which ones are considered most credible by management and which have the greatest potential impact on business.
Estimated annual business impact: The list of prioritized business consequences should be evaluated to determine an estimate of the annual business impact, ideally in financial terms. There are costs associated with implementing countermeasures to prevent or minimize a cybersecurity event. Unless there is a much larger cost to the business than the cost of countermeasures, it will be difficult to justify the cost of the countermeasures.
Cost: The purpose of the business rationale is to justify the anticipated cost of the human effort and technical countermeasures required to manage cyberrisks. The larger the difference between that cost and the estimated annual business impact, the easier it will be to justify allocation of resources. Estimating the cost of technical countermeasures should be straightforward. Estimating the cost of the human effort will be more challenging. Fortunately, ISA-62443-2-1 addresses all aspects of managing cyberrisks, including the most important one: people. The standard defines how to organize for security and provides guidance to help estimate the human effort required to manage cyberrisks.
First step
The cyberthreat scenario for critical infrastructure, including water and wastewater systems, is increasing and will become only more challenging in the future. The first step to creating a security plan is to define a business case for OT cybersecurity. By justifying the business rationale, a utility can reduce its cyberrisks, increase its resiliency, and ensure the availability and reliability of water and wastewater systems. ISA-62443-2-1 is a valuable resource for developing a cybersecurity management system that is essential for protecting critical infrastructure.
ISA offers standards-based industrial cybersecurity training, certificate programs, conformity assessment programs, and technical resources. Please visit the following ISA links for more information:
- ISA Global Cybersecurity Alliance
- Cybersecurity Resources Portal
- Cybersecurity Training
- IEC 62443 Conformance Certification
- Family of Standards
- ISA/IEC 62443 Cybersecurity Certificate Programs
- Suite of Security Standards
A version of this article also was published at InTech magazine.




