This post was authored by Steve Mustard, an industrial control system and cybersecurity consultant, and author of the ISA book Mission Critical Operations Primer, and Mark Davison, is a software engineer with more than 30 years of experience. Currently he is an owner/director of Terzo Digital.
Blockchain is a novel technology that leading industry players predict will cause major disruption to many existing industries, including banking, real estate, supply chain, voting, and energy management.
Large businesses, such as IBM, Samsung, UBS, and Barclays, are already working on blockchain-related projects and services, and hundreds of startup businesses are developing their own killer applications. Blockchain technology could also disrupt the industrial control system (ICS) world, so it is worth looking now to see what might be coming and how it might affect us.
Blockchain technology
Blockchain technology is a decentralized method for recording transactions. These transactions are recorded in a distributed ledger (known as the blockchain) that is stored across thousands of computers worldwide.
Transactions are recorded in the ledger and grouped together in blocks. They are secured using a form of cryptography called "hashing." Because the ledger is distributed and secured using hashing, it is theoretically impossible to make changes once something is recorded.
Hashing converts the data in a block into a hash, a format that cannot be decrypted to obtain the original data. It is unique such that any changes to the original data will yield a different result. Blocks in a blockchain incorporate the hash from the previous block, and so tampering with or forging transactions by changing data in a block is easily identified and prevented.

1) Someone wants to send money to someone else.
2) A block is created online to represent the transaction.
3) The new block is broadcast to all blockchain miners in the network.
4) The miners approve the transaction and validate it.
5) The block is then added to the blockchain, providing a permanent record. At this point, the transaction is valid. All miners receive a copy of the updated blockchain, making any discrepancies quickly evident.
6) The recipient receives the payment.
Where is blockchain used?
The best-known use of blockchain technology is in Bitcoin, a "cryptocurrency" that allows users to send and receive money electronically. Bitcoin uses blockchain technology to maintain a ledger of every Bitcoin transaction. A growing number of major businesses use Bitcoin, including Microsoft, Subway, and Whole Foods, as well as many small restaurants and traders. The total value of all existing Bitcoins now exceeds $20 billion (up from $2.7 billion in 2015), and millions of dollars are exchanged daily.
New Bitcoins are generated through a process called mining. This process involves individuals called miners, who use special software to "mine" blocks, or create the hash required to update the blockchain. Miners are issued a certain number of Bitcoins in exchange for this processing. Mining requires significant processing power to perform the hashing in order to conform to strict rules known as proof of work. The complex processing required to achieve the proof of work helps manage the rate at which Bitcoins are issued.
Hashing algorithms produce a fixed size output (called a hash code or digest), irrespective of the data being hashed. Bitcoin uses a secure hashing algorithm (SHA) with 256 bits (32 bytes) in its output, or SHA-256 for short. For example, the SHA-256 hash of "International Society of Automation" (35 characters) is:
75b8e883214c8543f22fcf1adb6682666f5308fcb
9dcc896846b2d53fba2141e
and the SHA-256 hash for "Automation Federation" (21 characters) is:
8da363f674c49fa3f5b4bbdfac92610d0906ad
e2d58f38a39c8ee8faa74bad91
The very first block in the Bitcoin ledger (called the genesis block) has the hash:
000000000019d6689c085ae165831e934f
f763ae46a2a6c172b3f1b60a8ce26f
In the proof of work process, the miner is presented with a number of pieces of data, including the SHA-256 hash representing the previous block in the chain; details of the current transactions to be processed, such as a timestamp (created by the miner); and information pertinent to the transactions themselves. The miner combines all this data into one hash. This is referred to as the challenge. The miner's task is to produce what is known as a proof, such that the SHA-256 hash of the challenge and proof results in a hash that has a fixed number of leading zeroes (out of the total 256 bits in the hash).
Due to the unique one-way nature of hashing algorithms, the only way the miner can determine the proof (also known as nonce, a term commonly used in cryptography for a number that is used only once) is to try all possible permutations until an answer is found. The number of leading zeroes in the hash determines the number of possible permutations. For example, if it were necessary to have the first 40 bits of the hash as zero, there would be approximately 1 trillion possible combinations (240). Varying the number of zeroes halves or doubles the amount of work (239 = 549 billion, 241 = 2.2 trillion).
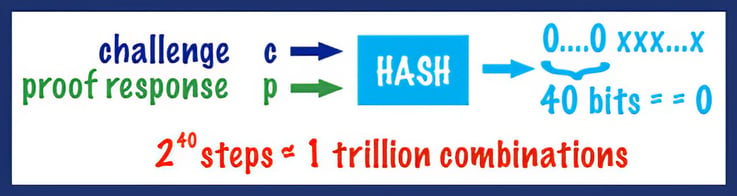
In Bitcoin, the proof of work is designed to take approximately 10 minutes to perform. At present, this results in a hash with 18 leading zeroes, or 262,144 possible permutations (218). Once a miner determines the proof, the resulting hash is stored in the transaction block, and this hash will be subsequently used in the processing of the next block.
The reasons why blockchain technology can successfully manage $20 billion of currency are also reasons why it can be useful in other transaction management applications:
- Due to its decentralized nature, blockchain technology does not have a central point of failure and is better able to withstand malicious attacks.
- Changes to public blockchains are publicly viewable by all parties, creating transparency, and transactions cannot be altered or deleted.
Bitcoin has perhaps gained more notoriety than respect from the general public to date, because hackers have used it to collect their fees from ransomware attacks. Bitcoin transactions involve transfers between anonymous addresses, and the lack of central control makes it difficult, but not impossible, to trace. However, blockchain technology can be a force for good.
Already disruptive
Blockchain technology is already being used in a wide variety of industries. More than $500 million was invested in venture capital-backed blockchain companies in 2016. Some high-profile applications include:
- The diamond industry to track individual diamonds from mine to consumer. This addresses counterfeiting, loss of revenue, insurance fraud, and conflict diamond detection.
- The medical industry to maintain a backup of a person's DNA that can be readily and securely accessed for medical applications.
- In retail to record every action that happens in a retail supply chain and make all the data searchable in real time for consumers. This allows the consumer to scan a QR code on a can in the supermarket and find out where the food inside was obtained, who certified it, where it was canned, etc.
- Legal to lock down a video or photograph, so it is impossible to change one pixel without a record of the transaction, allowing uses like recording indisputable insurance claims or police brutality.
- Energy management to allow customers to buy and sell energy directly, without going through a central provider.
Closer to home, IBM is working in partnership with Samsung to develop a decentralized Internet of Things (IoT). Autonomous decentralized peer-to-peer telemetry (ADEPT) uses blockchain technology to secure transactions between devices. IBM and Samsung are planning networks of devices that can autonomously maintaining themselves by broadcasting transactions between peers, as opposed to the current model of all devices communicating only with centralized, or cloud, services.
Central to this concept is the registration of IoT devices in a publicly maintained blockchain, creating a level of trust that cannot be achieved for rogue devices.
ISA offers standards-based industrial cybersecurity training, certificate programs, conformity assessment programs, and technical resources. Please visit the following ISA links for more information:
- Cybersecurity Books
- Cybersecurity Training Courses
- Cybersecurity Blog Posts
- Cybersecurity Resources Portal
- ISA Global Cybersecurity Alliance
- IEC 62443 Conformance Certification
- ISA Suite of Security Standards
- ISA Family of Standards
- ISA/IEC 62443 Cybersecurity Certificate Programs
Blockchain in the ICS world
Blockchain technology has other potential applications for ICS, such as the protection and verification of device firmware and application software updates. As ICS users have secured their networks, attackers have taken to other methods to infiltrate systems. One such method involves inserting Trojan malware into ICS software that is downloaded by users for installation on their networks. In 2014, a variant of the malware Havex contained code that scanned networks for OPC-aware devices. It then collected information on the tag configuration and uploaded it to an external server. This Trojan was found in downloadable software on ICS vendor websites. Registering firmware and software in a blockchain could provide an immutable record of code, making an attack like the Havex OPC example impossible. Other potential ICS-based applications are:
- authentication, authorization, and nonrepudiation of device configuration and program changes
- protection, verification, and nonrepudiation of critical data, such as historian streams or regulatory reports
Challenges
One of the challenges for the non-Bitcoin blockchain solutions is that a key benefit of a truly distributed ledger is only achievable if there is some obvious financial gain for miners. The above examples, such as the ICS firmware or software ledger, may only be achievable with a private (e.g., run by one ICS vendor for their products only) or consortium blockchain (perhaps managed by a collective of ICS vendors). In this application, there may still be some concerns about the security of the ledgers, but in the case of ICS firmware and software verification, a private or consortium blockchain would still provide significantly more assurance than existing methods.
As with all disruptive technologies, it is impossible to predict with certainty what will happen. All we can do is watch this space. What is certain is that blockchain technology is not going away anytime soon.
Learn more about industrial security and mission critical operations. Click this link to download a free 48-page excerpt from Mission Critical Operations Primer.
About the Author
Steve Mustard, author of the ISA book, Mission Critical Operations Primer, is an independent automation consultant and subject-matter expert of ISA and its umbrella association, the Automation Federation. He also is an ISA Executive Board member. Backed by nearly 30 years of software development experience, Mustard specializes in the development and management of real-time embedded equipment and automation systems, and the integration of real-time processing, decision-support and other disparate systems to improve business processes. He serves as president of National Automation, Inc. Mustard is a recognized authority on industrial cybersecurity, having developed and delivered cybersecurity management systems, procedures, training and guidance to multiple critical infrastructure organizations. He serves as the chair of the Automation Federation’s Cybersecurity Committee. Mustard is a licensed Professional Engineer, UK registered Chartered Engineer, a European registered Eur Ing, an ISA Certified Automation Professional (CAP) and a certified Global Industrial Cybersecurity Professional (GICSP). He also is a Fellow in the Institution of Engineering and Technology (IET), and a senior member of ISA.
About the Author
Mark Davison is a software engineer with more than 30 years of experience. Currently he is an owner/director of Terzo Digital, a software consultancy firm specializing in IoT and telemetry. Davison is a current committee member for the Water Industry Telemetry Standards (WITS) Protocol Standards Association, helping to develop new standards in the IoT arena, aimed at more than just the water industry.
A version of this article also was published at InTech magazine.



