This article was written by Mohammed A. Al-Saeed, Soliman Al-Walaie, Khalid Y. Alusail and Turki K. Al-Anezi, of Saudi Aramco.
Supporting business needs by improving defense-in-depth cybersecurity for industrial automation and control systems (IACSs) is a key challenge today. For example, oil, gas, and water plants need to access scattered and remote areas and wells, but cybersecurity can be a major challenge, which may require physical security and cybersecurity protections and controls. Therefore, wireless technology, such as 4G (long-term evolution [LTE]), is becoming the standard platform for Internet service provider cellular networks. In addition, it is being introduced to serve industrial applications. Its reliability may satisfy industrial business needs and connect many sites and plants easily to minimize cost and increase flexibility.
The main aspects of cybersecurity in wireless and LTE are privacy and confidentiality because of common attacks in a shared medium. For instance, passive attacks (eavesdropping, physical layer attacks, radio frequency jamming) and active attacks (hacking and man-in-the-middle attacks) are common challenges in the wireless domain. Therefore, robust mutual authentication and encryption mechanisms will protect an IACS. This was clearly demonstrated in the proof of concept (POC) conducted to test security solutions and controls of LTE wireless technology for IACSs, such as supervisory control and data acquisition (SCADA) systems and closed-circuit television (CCTV). A Yokogawa SCADA system (remote terminal unit [RTU] and SCADA host) was used as a SCADA platform, and a Huawei e-LTE broadband multimedia digital wireless system as a communication platform. The POC setup and evaluation, at King Fahd University of Petroleum and Minerals Communications Lab on 26 January 2015, used several cybersecurity solutions, such as firewalls; virtual private network, Internet Protocol security (VPN with IPSec); generic routing encapsulation (GRE); virtual local area network (VLAN) between different industrial/plant applications (RTU, voice terminal, CCTV, and FTP); encryption AES 128; and physical security (CCTV monitoring system). The throughput of industrial applications decreased by 30 percent with an aggressive IPSec encryption and a GRE tunnel. In conclusion, 4G (LTE) technology with effective security controls and optimized design has the capability and capacity to serve voice, video, and broadband industrial data and applications simultaneously.
4G (LTE) wireless security
Generally, oil and gas operations are spread across large geographical areas, and workers at centralized control centers manage and operate day-to-day field operations, which are subject to harsh environmental conditions. SCADA systems electronically monitor and manage remote operations using advanced operational technology/information technology (OT/IT) solutions. In the “old days,” and even today, ultrahigh frequency (UHF) radios connected field RTUs via low-speed serial interface (RS232) radio channels that did not exceed 25 kHz, which the UHF modems use to modulate SCADA signals at roughly 19.6 kbps. This approach is adequate for the SCADA host to pull data from field devices and send supervisory control commands, such as a close/open command to a valve and a start/stop command to a pump, to the field. High speed is needed whenever there is an asset management solution for diagnostic purposes. In general, wireless communication is allowed for noncritical SCADA monitoring applications, and there should be a physical and logical segregation from non-SCADA applications in terms of network, communications hardware, servers, etc.
 Figure 1. Industrial wireless systems requirements
Figure 1. Industrial wireless systems requirements
RTU capabilities have advanced significantly in support of intelligent operations, intelligent field, CCTV, mobile radios with cameras, field data connectivity, and other applications. Such applications require broadband connectivity, and the 4G (LTE) has the potential to satisfy all the aforementioned applications (figure 1).
The ISA100, Wireless Systems for Automation Committee grouped wireless applications into three classifications: monitoring, control, and safety (figure 2). Wireless technology is becoming very popular for instrumentation (ISA100.11a) as well as for backhaul long-range process automation connectivity (ISA100.15).
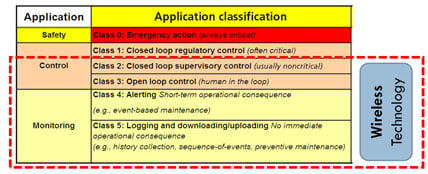 Figure 2. Industrial wireless systems classifications
Figure 2. Industrial wireless systems classifications
A collaboration of national and regional telecoms standards bodies, known as the Third Generation Partnership Project (3GPP), developed LTE. LTE evolved from an earlier 3GPP system, the universal mobile telecommunication system (UMTS), which in turn evolved from the global system for mobile communications (GSM).
4G (LTE) technology has the potential to concurrently serve several industrial applications, such as:
- oil and gas SCADA systems
- cathodic protection monitoring and control
- CCTV remote surveillance and alerting
- mobile voice/video conferencing
- energy management
- wastewater management
- vibration monitoring
- power monitoring systems
- microseismic sensing and intelligent field applications
4G (LTE) security overview
To understand the security architecture of the LTE, you need to know the LTE components and how these components communicate with each other and outside the LTE network. From a high-level network architecture point of view, LTE consists of the following three main components:
- user equipment (UE) or customer premises equipment (CPE)
- evolved UMTS Terrestrial Radio Access Network (EUTRAN)
- evolved packet core (EPC)
These components communicate with each other via standard interfaces.
EUTRAN is the LTE access layer, and EPC is the core layer. The 3GPP segments the LTE security architecture into five functional domains; 3GPP TS 33.401 defines these domains as follows:
- Network access security uses universal subscriber identity module (USIM) to provide secure access for a user to the evolved packet system (EPS). It includes mutual authentication and privacy features.
- Network domain security refers to features that allow secure communications between the EPS and EPC nodes to protect against attacks on the network.
- User domain security secures access to the terminal, such as a screen-lock password and PIN, to enable USIM usage.
- Application domain security is the security features used by applications, such as HTTP.
- Visibility and configurability of security tells a user whether or not a security feature is in operation, and gives user-configured control over whether the use of a service depends on enabled security features.
UE stores user and device confidential information. For UE to be able to communicate with a 4G (LTE) system, it has to register with the access layer. This is called user-to-network registration, and it has to be secured. It is important to notice that data traffic carried over LTE is not encrypted end to end, which makes it subject to being captured by a nontrusted entity at certain points. Encryption starts at the end-user device and terminates at the network side, whereas in 3G, data encryption starts at the end-user device, crossing the network all the way to the radio network controller.
LTE traffic leaving the access layer from eNodeB to the core layer mobility management entity (MME) or serving gateway (SGW) utilizing the S1 interface will be sent in clear text. In this case, customer private information might not be protected.
In the early deployment of LTE, it was possible to send the mobile subscription identification number, which contained some private user information, to the network in clear text if no IPSec solution was in place between the access layer and core layer.
Security POC
For the POC setup and evaluation at King Fahad University of Petroleum and Minerals, analysts used the Yokogawa SCADA system (RTU and SCADA host) as a SCADA platform with simulated I/O points. A Huawei e-LTE broadband multimedia digital wireless system was the communication platform serving different applications. SCADA setup included a Yokogawa Stardom RTU (figure 3) with the following criteria:
- three process variables
- DNP3 protocol
- 1 millisecond scanning resolution
- 1 second polling
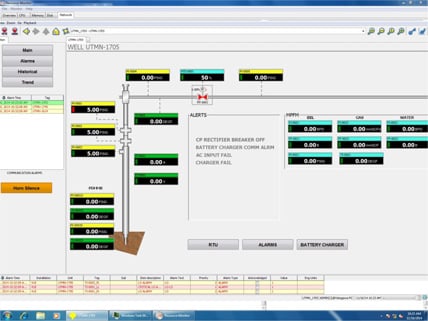 Figure 3. SCADA setup
Figure 3. SCADA setup
The test specifications were:
- The operating frequency and channel bandwidth was 1.8 GHz and 20 MHz.
- The access mechanism was TD-LTE (OFDMA/SC-FDMA).
- The quality of service and carrier-to-interference ratio settings were guaranteed bit rate.
- There were two indoor antennas.
- The distance was short; cell setup was 1 km.
- The signal-to-noise ratio was 20+ dB.
- Camera specifications were 1280*720, 720p.
- The simulated protocol was TCP/IP and UDP.
- The testing tools were Yokogawa SCADA host and RTU, Huawei NMS/HiStudio, and Iperf.
- Security requirements for LTE solutions included access control, encryption, and physical security domains.
- There was logical segregation using VLAN between different industrial/plant applications (RTU, voice terminal, CCTV, and FTP).
- There was logical segregation using VLAN between different sites (each CPE and antenna had different VLANs)
- A firewall with routing capability or a dedicated router prevented access between each site.
- A firewall prevented access between different applications within the site.
- VLAN 1 was for management and maintenance.
- VLAN 20 was assigned to the RTU of site 1.
- VLAN 30 was assigned to the FTP client.
- VLAN 40 was assigned to CCTV.
- VLAN 41 was assigned to the SCADA host only.
- VLAN 42 was assigned to the FTP server.
- VLAN 30 was assigned to the video/camera server.
- A VPN was established by using IPSec between the remote site firewall and the central firewall.
- A GRE tunnel was established between the CPE and the central router.
- AES 128 encryption was used for the LTE connection.
- A CCTV monitory system was used for physical security protection.
Security test case results
- When the SCADA service is running, the SCADA host cannot access the CCTV server/camera and FTP server/client.
- When the video service is running, the CCTV server cannot access the SCADA host/RTU and FTP server/client.
- When the video service is running, the CCTV server cannot access the SCADA host/RTU and FTP server/client
- When the FTP service is running, the FTP server cannot access the SCADA host/RTU and CCTV server/client.
- The throughput of the system decreased by 30 percent using IPSec and GRE tunnel.
Security observations
- LTE technology with effective security controls, such as VPN (IPSec) and GRE, can serve voice, video, and broadband industrial data and applications simultaneously.
- 4,000 IPSec tunnels can be configured on the firewall, USG 6370. Therefore, the firewall can support up to 4,000 remote field sites.
- The system throughput decreased by 30 percent using an IPSec tunnel and GRE tunnel.
- The POC proved that a secure LTE wireless platform can serve multiple IT and OT systems, such as SCADA and CCTV applications, and allocate the required resources.
LTE reliability can connect many sites to minimize cost and increase flexibility. The POC clearly demonstrated that mutual authentication and encryption mechanisms protect IACSs, showing that 4G (LTE) technology with effective security controls can serve voice, video, and broadband industrial data and applications.
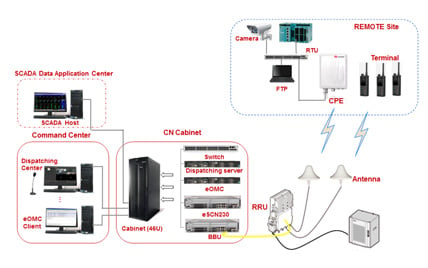 Figure 4. General network layout
Figure 4. General network layout
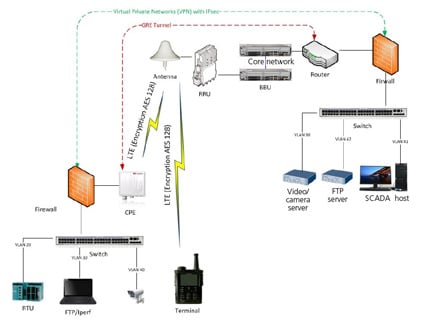 Figure 5. POC security test design
Figure 5. POC security test design
About the Authors
Mohammed A. Al-Saeed is a network and systems specialist at Saudi Aramco in the process and control systems department, plants network unit. He has 20 years of experience in IT/OT. Al-Saeed is an ISA member in the ISA99 and ISA100 groups.
Soliman Al-Walaie is a communication engineering consultant in the process and control systems department of Saudi Aramco with more than 17 years of experience in industrial networks and IT technologies.
Khalid Y. Alusail has more than 20 years of experience in the IT field across the value chain. Currently, he works with the process and control systems department, plants network unit, at Saudi Aramco.
Turki K. Al-Anezi is an engineer in the process automation systems unit with 20 years of experience in the field of process automation, control systems, and instrumentations at Saudi Aramco. Al-Anezi is the subject-matter expert for pipeline leak detection, SCADA systems, and RTUs.
A version of this article also was published at InTech magazine.



